Cyberbullying Analysis on WhatsApp Messenger Using the National Institute of Justice (NIJ) Method
on
p-ISSN: 2301-5373
e-ISSN: 2654-5101
Jurnal Elektronik Ilmu Komputer Udayana
Volume 9 No. 4, May 2021
Cyberbullying Analysis On WhatsApp Messenger Using The National Institute Of Justice (NIJ) Method
I Putu Denny Indra Putraa1, I Ketut Gede Suhartanaa2
aInformatics Department, Faculty of Math and Science, Udayana University
Bali, Indonesia
Abstract
Social media is no stranger to today's digital era. Many people prefer to use social media because of its simplicity and safety, This is what makes social media more popular than other services. However, because of its convenience and security, social media, especially WhatsApp Messenger, are vulnerable to crime, one of the most common is cyberbullying. For this reason, a mobile forensic investigation is required to find evidence related to cyberbullying. In this study, the National Institute of Justice (NIJ) method was used to investigate the WhatsApp Messenger platform used for cyberbullying. The NIJ method has 5 (five) stages to carry out the forensic process, namely Preparing, Collection, Examination, Analysis, and Reporting. This study also uses 3 assistance from software, namely MOBILedit Forensic, DB Browser for SQLite, and Odin3. This research is expected to be able to help solve the problem of cyberbullying and other crimes found on social media, especially WhatsApp Messenger.
Keywords: Media Sosial, WhatsApp, Mobile Forensic, Cyberbullying, NIJ
In today's digital era, most people are familiar with social media. Social media is a medium on the internet that allows users to represent themselves and interact, cooperate, share, communicate with other users to form virtual social bonds [1]. It cannot be denied that many people in Indonesia use social media, This can be seen from the research data conducted by We Are Social in 2020, 160 million or 59% of active social media users in Indonesia out of 272.1 million total population in Indonesia.

Figure 1. Data on Internet and Social Media Trends in Indonesia January 2020
There are various kinds of social media platforms in Indonesia, one of which is WhatsApp Messenger. WhatsApp Messenger is a mobile application that allows the exchange of messages, video, audio, and pictures via mobile [2] for free. This platform requires the help of the internet so that users can communicate with each other.
However, with this convenience, some people take advantage of social media, especially WhatsApp Messenger, to commit crimes in cyberspace. Crimes committed in cyberspace are often referred to as cybercrime, the crimes vary, such as cyberbullying, data theft, hacking, and so on. To solve a similar problem, forensic action on WhatsApp Messenger is needed, so that the problem can be solved.
It is hoped that the research carried out can help solve problems, especially on cyberbullying problems on WhatsApp Messenger social media. This study uses the National Institute of Justice (NIJ) method and uses MOBILedit Forensic software and DB Browser for SQLite. MOBILedit Forensic Is a forensic software that allows investigators to logically obtain, search and examine cell phone devices [3], while DB Browser for SQLite is software used to perform analysis and search for forensic evidence stored in a database [4].
This research uses the National Institute of Justice (NIJ) method. This method is used to explain the stages of research that will be used as a guide in solving a problem [5]. The following is an illustration of the stages of this research.

Figure 2. The National Institute of Justice (NIJ) Method stages
There are 5 (five) stages in this research that are used to carry out the forensic process, namely:
-
a. The preparation stage is the stage where the researcher prepares equipment to support the research process, such as laptops, MOBILedit Forensic software, DB Browser for SQLite software, and Odin3 software.
-
b. The Collection stage is the activity of collecting and documenting evidence, wherein this study, the evidence is obtained in the form of the perpetrator's smartphone.
-
c. The Examination stage in this study is to check the data contained on the perpetrator's smartphone, but before that, we have to check whether the smartphone is rooted or not. If not, then you can use the Odin3 software to root your smartphone. After that, data checking can be done with the help of MOBILedit Forensic software.
-
d. The Analysis stage is the stage where the researcher analyzes the data that has been previously obtained during the examination stage. The data obtained is in the form of a database with SQLite format, so you need help from the DB Browser for SQLite software to read the contents of the database. After that, the data will be analyzed technically and legally to be able to prove the data.
-
e. The Reporting stage is the activity of making a report that will be carried out after digital evidence is obtained from previous processes, this report will include the results of the analysis in detail, including the actions taken during the investigation, the tools and methods used.
This study uses case examples related to cyberbullying crimes. In this simulated case, there are 2 (two) users who use WhatsApp Messenger social media, namely user A (victim) uses a
smartphone with the brand IPHONE 7+ with the A1661 model and user B (the perpetrator) uses a smartphone with the SAMSUNG brand GALAXY GRAND PRIME model. User A has an account name "Denny Indra" while user B has an account name "Isthu Canistya". With the WhatsApp Messenger social media, the two users carry out chat activities both in the form of text messages and picture messages. However, user A feels annoyed with the contents of the message sent by user B, it turns out that the message received by user A is bullying. Furthermore, user A reports the incident to the authorities and after being traced, the incident becomes a cyberbullying case. After that, the authorities confiscated the SAMSUNG brand smartphone with the GALAXY GRAND PRIME model owned by user B, this confiscated item will be investigated further. In this investigation, the authorities used the National Institute of Justice (NIJ) method which has 5 stages for the forensic process.
At this stage, the authorities prepare all the equipment that will be used during the investigation process. The equipment used can be seen in the table below.
Table 1. Equipment used
|
No |
Equipment |
Specification |
Information |
|
1 |
Laptop |
ASUS VivoBook 8550U Intel Core i7, Windows 10 64bit |
Hardware |
|
2 |
MOBILedit Forensic |
Program version 9.0.0.21797 |
Software |
|
3 |
DB Browser for SQLite |
Program version 3.12.0 |
Software |
|
4 |
Odin3 |
Program version 3.07 |
Software |
In this second stage, the authorities are required to collect evidence, both physical items and data contained in the physical goods and their documentation.
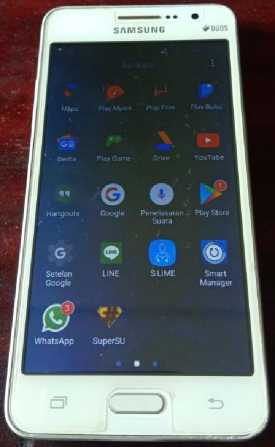
Figure 3. Perpetrator's Smartphone
The image above is a documentation of the physical evidence of the smartphone used by the perpetrator to carry out cyberbullying. The smartphone used by the perpetrator uses the Android
Operating System version 5.0.2 in a state that has not been rooted. After that, the authorities will take the data in the smartphone by duplicating it, this is so that the original data does not change or is damaged because the original data will later be used as digital evidence.
In this third stage what must be done is to check the data contained on the perpetrator's smartphone but before doing that, the authorities must first check whether the smartphone is in root condition or not, if not then the smartphone must be rooted first. Root functions so that users can control or have full access to their smartphone.
Here the authorities use the help of the Odin3 software already installed on the laptop to root the smartphone. If the smartphone is connected to a laptop, the rooting process can be done.
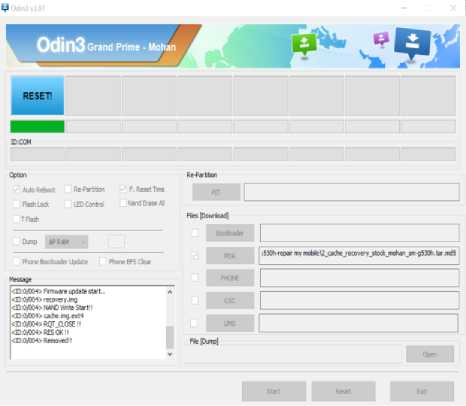
Figure 4. Root Process on The Perpetrator's Smartphone with Odin3 Software
If the smartphone is in root condition, then the inspection process can be done. The examination here uses the help of the MOBILedit Forensic software which is already installed on the laptop, the authorities only need to connect the perpetrator's smartphone with the laptop, if so, the image will appear as below.
-
□ Samsung Galaxy Grand Prime (Read-Only)

Conrwcted to USB Android 9SA8568C

Manufacturer: Samsung
Model: Galaxy Grand Prime
Operator Indonesia (510) TEIKOMSEL (10) Tsel
-PakaiMasker
Phone time; 22/09/2020 8:46:42 carta
IMEi: 357700060930512
Serial Nr., 95a8568c
MSISDN: +628113921008
ICCID: 8962101039132077040
IMSI: 510103913207704
Software revision: 5.0.2 (21)
Connected via: Forensic Connector 1.1√45-21797(F)
Networks: GSM
B®
[⅛ Uninstall Connector Report Wizard
Q® Memory dump io Screenshot
8:46:42 carra 22/05/2020 Platform: Android
IMEI: 357700060930512
-
Figure 5. Information About the Perpetrator's Smartphone
In the examination process, apart from obtaining information about the perpetrator's smartphone, the authorities also obtained various types of data contained on the perpetrator's smartphone such as contacts, galleries, applications, and so on. For more details, see the image below.
! ≡ Applications (207) - Samsung Galaxy Grand Prime
|
*,,wna P Il u∣ |
πlB I orwwic U < CIWierIo |
X Googlo IlH Play owv∣ |
β "'n, |
□ IX |
gj WhawAp |
I AASAwrv ∣α |
I Aqon I Masukan |
j Aleml | |||
|
PJl I Baria* kJ I Agent |
I Buikup ∣ and Real |
M I BadgePro H I VHtei |
0 |
BKAgen |
— I Bwbagl ~ I Wi FiDu |
•1 |
Bkjetool h |
I Bluwoot I Iifest |
∣^∙ |
ICapliveP I OrtaILogi | |
|
I cσrτwndr |
I comandr |
I com goal |
I |
com.qual |
I oomgual |
SRI |
com sum |
I com,sam |
I com.sec,a |
I com SPC.I | |
|
I ahi .Uuιro |
∣ nlιl wnll∣ι |
∣ RNnmlInI |
cornm.qc |
I COtIttIutI |
SLirigand |
I su ng.and |
I gll.maker |
j ndrold Uf | |||
|
m Cuaca |
Mkl DevKe Protectlo |
∣ Di-ottKe ∣P∣⅛9 |
DevlceIes |
ru∣∣ DiagMon |
1^I |
Dialer |
LR>kι∣men |
M I DRftasw I Mode |
BIX | ||
|
∣∣ I Error |
^ IiIeSay4 |
I Fused ∣ location |
3 |
Galeri |
I Googlo I Baikup Ii |
^L∣ HwModM 'I"' |
I Iniomiasi I Knamwia |
O Jam | |||
|
I Ka∣∣ιu,: ∣ Penggun |
I Kendall Ijarakjauh |
I KendaA ∣ jarak Jauh |
⅛ |
Kendall JarakJauh |
■■ I Kendall HI Ijarakjauh |
KeraJin wι |
I |
Kwangkii |
I Ketarigka I KeiJa Uy |
I Kw Jawln | |
|
Q I KNOX |
P I KNOX |
0 ∣ KNOX I' |
• I |
KNOX SrtupWIr |
Mj I Knorfoid “ I UfConialn |
A. |
Kontak |
• |
Kontak Fnvnrt |
/Si I Komroi ‰» I interaksi |
I Lwnunwi J Dmw |
|
m∣ l Mwrin |
∣ MinsSwvI |
I Mobile ∣ ιιackw |
® |
MuHimed Ia Ul Seiv |
HH J ∏MACP |
≡ |
Pbaiuan pmgkat I |
PacPioce |
AI MeBud dyNotιSv |
∣ Rviduaii I penyetek | |
|
HI PnnuWi Γ ri Mnlipapw |
. I Pbmutai ' ∣ Video |
I Penampll I FlTML |
«I |
Pondaliar |
®ir |
e |
Pengatur |
Pengeiola Aksm Go |
⅛∣≈ |
I', '"l"'"' KZ kwluSIM | |
|
~ I Periylmpe “ 11 non Kont |
I Penyimpa ∣ n4∏ Medi |
∣aa I IMnyimpa ∣ nan peng |
Ol |
Penylmpa narι peng |
I Pwaiigka I I Masuka |
□I |
Pwekwn |
Pe∣men |
∣∣ I Perso |
^∣ Pesan | |
|
I RCPCom ≡ I POIWtlI |
∣ ringtone ∣ backup |
∣ RoolPA |
s |
RoseFtlK |
^ Nannii |
ED |
S Planner |
0 |
— I Samsung ≡ I Billiiej |
∣t∣∣^Γ | |
|
I ⅛Def⅛∣l ∣ Claundw |
∣ SfcntLog ∣9∣∏a |
M∣ Slnkronis ∣ an Googl |
31 |
SlnkrOtMs Mi Googi |
« I Sstem I Android |
& |
Manager |
0 |
d Manage |
I Smaitcar I dSwvlce |
j SOAgant |
|
I Rpcliimp ∣ Service |
Kll w°,' |
K] ' ,⅛pon |
H |
I⅛ιpoι> |
Clj Tema |
[ |
Tetheting Autamatl |
0 |
FoudiWii dop an |
mm I Ul sistem |
Jl ⅛w5 |
|
I Wrwd ∣ Penylapa |
I WIwiTwe |
U∣ Aridiold W ACCHSIbII |
O |
Android |
l^ Chrome |
e» |
Currents |
O |
Drive |
^ i . ιLuy |
Q Gmail |
|
Google ⅞ * Play Mum |
Ptay Slot |
0’ Hangouts |
A |
Loyaruin Googkt Pl |
ς> IlNE |
⅛ |
Maps |
E |
Googht T |
WSUME |
«k Samsung ■■ <∙lt Mdo |
-
Figure 6. Results of The Perpetrator's Smartphone Check
In the picture above, there is a WhatsApp Messenger application that was used by the perpetrator to do cyberbullying, so the authorities will immediately carry out further checks on files from the WhatsApp Messenger application which are already in the form of a folder with the name "com.whatsapp", this folder can be found in the directory as follows:
data÷data÷com.whatsapp
When viewed from the MOBILedit software, this is the contents of the WhatsApp Messenger folder (com.whatsapp).
|
File Name ®app_minidumps |
Size <folder> |
Created 19/09/20... |
Modified Accessed 19/09/20... |
|
& app textures |
<folder> |
21/09/20... |
21/09/20... |
|
≡ app_webview |
<folder> |
22/09/20... |
21/09/20... |
|
• cache |
<folder> |
22/09/20... |
19/09/20... |
|
® databases |
<folder> |
22/09/20... |
19/09/20... |
|
& files |
<folder> |
22/09/20... |
19/09/20... |
|
s lib-main |
<folder> |
19/09/20... |
19/09/20... |
|
*no_backup |
<folder> |
19/09/20... |
19/09/20... |
|
® shared_prefs |
<folder> |
22/09/20... |
19/09/20... |
|
lib |
<unknow... |
<unknow... |
22/09/20... |
Figure 7. WhatsApp Messenger Application Folder (com.whatsapp)
In the picture above, there are 9 sub-folders and 1 file with the name “lib”, the number of folders depends on the use of the WhatsApp Messenger application. Next, the authorities will check every sub-folder contained in the “com.whatsapp” folder. From the results of the examination, several files were obtained in the form of a database with SQLite format. To find out the contents of the file, the authorities will open it with the help of DB Browser for SQLite software for further analysis.
In this fourth stage, the authorities will analyze the database with the SQLite format that has been obtained with the name "msgstore.db". From the analysis using DB Browser for SQLite software, there are 112 tables in the database "msgstore.db", which can be seen in the image below for more details.
H DB Browser for Stll ite - D ∖SNATlA∖⅛abases∖msgstore db Elle Edit ⅛iew Tools Help
u New Database # Open Database ι ,.∣t∣!∣√u- ⅛1∣'tiv∣ ^ # Ooeri Project : Save Project «,Attach Database XOoseDatabase
Databasestruaure Browse Data EcSt Pragmas ExeculeSQL IjCreateTabie ⅛Create Index ι⅛Print
Name Type
* J Tables (112)
> it away,messages
> C callj⅛g call Jog_part>apant_v 2 > ⅛ chat > ⅛ ChatJist > Ol conversion-tuples > E∣ deleted-ctratJob > ∣il frequent > l!∏ frequents
-
> 0 groupJrotificationverskin
-
> al groupj>⅛rtiσpant .device
-
> EJ group partidpant user
-
> ΣI groupjMttidpaιιts
J J gι Oupjxart IopantS-History
-Jid
-
> IflJ keywords
-
> u IabeIedJrd
-
> S IabetedJids
-
> EJ labeled,messages
-
> Ji Iabeled-HiessagesJts
-
> I JabetedjiiesSagesJtS-Co...
-
> J labeled messagesJts.se...
∣' J labeled-messagesJts _se..
-
> EJ labels
J ιτιedia.hash-thιιmbnail
-
> J r∏edi∙a.refs
Schema
CREATE TABLE away.messages (Jd INTEGER PRIMARY KEV AUTOlNCREMENLjid TEXT UNIQUE NOT NULL)
CREATL TABLE calljog ( .id INTEGER PRIMARY KEY AUTOINCREMENT, jid.row.id INTEGER, from.me INTEGER, call.id TEXT, transa CREATE TABLE call Jog.partιdpant.v2 (Jd INTEGER PRIMARY KEY AUTOINCREMENT, CallJogjowJd INTEGEKjidjowJd INTEGEI CREATE TABLE chat {Jd INTEGER PRIMARY KEY AUTOINCREMENTjid .row.id INTEGER UNIQUE1Hidden INTEGER,subject IEXTjreaI CREATE TABLE ChatJist (.id INTEGER PRIMARY KEY AUTOINCREMENT. IceyjemoteJid TEXT UNIQUE, message JabIeJd INTEGER.: CREATE TABLE Conversionjuples (jid.rowjd INTEGER PRIMARY KEY, data TEXT, source TEXT, biz.count INTEGER, has .user .sent Ia CREATE TABLE deleted.chatjob ( jd INTEGER PRIMARY KEY AUTOINCREMENT, chatjow.id INTEGER NOT NULL, block size INTEC CREATE TABLE frequent Ud INTEGER PRIMARY KEY AUTOINCREMENT, jidjσw.id INTEGER NOT NULL type INTEGER NOT NULL r CREATE TABLE frequents (Jd INTEGER PRIMARY KEY AUTOINCREMENT, jid TEXT NOT NULL, type INTEGER NOT NULL message.c CREATE TABLE group.notificati∙on.verssoπ IgroupjidjowJd INTEGER PRIMARY KEY, SubjectJimestartip INTEGER NOT NULL ann< CREATE TABLE group-partidpa∏t-device LW INTEGER PRIMARY KEYAUrOINCREMENL groupjwrticipantjow.id INTEGER NOT H CREATE TABLEgroupjMrticipant-Usef (Jd INTEGER PRIMARY KEY AUTOINCREMENT, groupjid rowjd INTEGER NOT NULL us«j CREATE TABLE gr□upj>aιtιcipants Lid INTEGER PRIMARY KEY AUIOiNCREMENT. gjid TEXT NOT NULL, jid TEXT NOT NULL admin CREATE TABLE group_partkipants-history Lid INTEGER PRIMARY KEY AUTOINCREMENT, timestamp DATETIME NOT NULL gjid TI CREATE TABLEjid (Jd INTEGER PRIMARY KEY AUTOINCREMENT, user TEXT NOT NULL, server TEXT NOT NULL, agent INTEGER, de CREATE TABLE keywords Lid INTEGER PRIMARY KEY AUTOINCREMENT1 keyword TEXT UNIQUE NOT NULL)
CREATE TABLE IabeIedJtd LW INTEGER PRIMARY KEY AUTOINCREMENT, IabelJd INTEGER NOT NULLjidjowJd INTEGER NOT NI CREATE TABLE IabetedJids (Jd INTEGER PRIMARY KEY AUTOINCREMENT. IabeLid INTEGER NOT NULLjid TEXT)
CREATE TABLE labeled, messages (id INTEGER PRIMARY KEY AUTOINCREMENT, IabeIJd INTEGER NOT NULL ImessagejowJd IN CREATE ViRTUALTABLE IabeledjriessagesJts USING FT53Q
CREATE TABLE labeled ,messages Jts.content'(docid INTEGER PRIMARY KEY. 'cθcontent')
CREATE TABLE labeled ,messages Jts. segdir'(level INlEGER1Idx INTEGER,start.block INTEGER, leaves.end.block INTEGER.end,blod CREATE TABLE 'IabeledjnessagesJts_segments'(blockid INTEGER PRIMARY KEY. block BLOB)
CREATE TABLE labels L∙d INTEGER PRIMARY KEY AUTOINCREMENT, IabeLname TEXT, predefined Jd INTEGER, colorJd INTEGER) CREATE TABLE UiediaJiashJhumbnaa ( media.hash TEXT PRIMARY KEY. thumbnail BLOB)
CREATE TABLE media refs (Jd INTEGER PRIMARY KEY AUTO∣NCREMENL path TEXT UNIQUE, r√ count INTEGER)
Figure 8. Table Structure in Database "msgstore.db"
First of all, the authorities want to know the messages from anyone on the perpetrator's account. So that the authorities will open the messages table in the DB Browser for SQLite software, and get the following results.
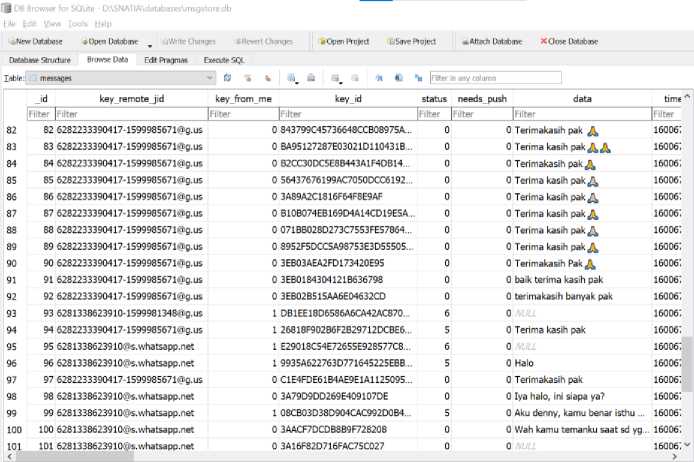
Figure 9. The Contents of The messages Table
From the picture above, we can get several conversations from the perpetrator with other accounts. But what is most needed is a conversation between the perpetrator and the victim. From some of these conversations, we get a message that says “Aku denny……”. For that, a filter is needed so that you can find out the entire message of the conversation.
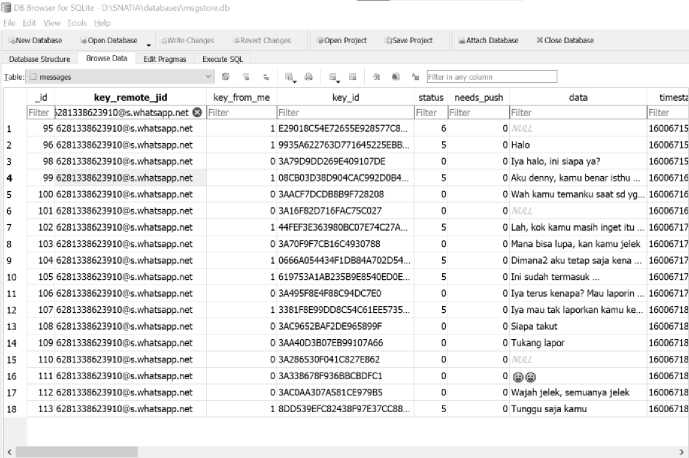
Figure 10. The Contents of The messages Table after Filtering
In the picture above, there is a conversation between the perpetrator and the victim who has the attribute "6281338623910@s.whatsapp.net" in the column "key_remote_jid". In the conversation between the perpetrator and the victim, there are messages that are bullying that the perpetrator throws at the victim and there are several messages that the DB Browser for SQLite software cannot get, this can be seen in the data column which only displays NULL.
From the results of this analysis, the conversation between the perpetrator and the victim can be used as digital evidence for cyberbullying cases by using the WhatsApp Messenger social media as the platform.
In this study using the National Institute of Justice (NIJ) method, this method has 5 (five) stages in the forensic process. The first stage is Preparing, at this stage, the authorities will prepare digital equipment in the form of laptops, smartphones, MOBILedit Forensic software, DB Browser for SQLite software, and Odin3 software. Continue at the second stage, namely Collection, the authorities will collect evidence both physical goods and data contained in physical goods, after obtaining the evidence, it will be duplicated so that the original evidence is not changed or damaged. Entering the third stage, namely Examination, before carrying out further checks, the authorities must confirm whether the smartphone is in a root condition or not, if not then the smartphone will be rooted with the Odin3 software. If you are already in the root condition, you can also check the data contained on your smartphone, the authorities use 2 (two) pieces of software, namely MOBILedit Forensic and DB Browser for SQLite. MOBILedit Forensic functions to process smartphones, both extracting and acquiring data contained in the smartphone, the authorities also find folders and files contained on WhatsApp Messenger (com.whatsapp). From the results of the folder inspection, there were 9 sub-folders and 1 file with the name "lib". After further examination, important data is obtained with the name "msgstore.db", "msgstore.db". This is a data storage place in the form of a database in SQLite format. The authorities use the second software, namely DB Browser for SQLite to open the database. After opening, there are 112 tables in the database. Kemudian pihak berwajib langsung memeriksa tabel messages, dari analisis ini didapatkan beberapa percakapan dari pelaku. After further investigation, a bullying message was obtained between the perpetrator and the victim, and this message will later be used as digital evidence for further processing.
The goal of this research is to help solve cyberbullying problems on social media, especially WhatsApp Messenger, by means of mobile forensics using the National Institute of Justice (NIJ) method and using the help of MOBILedit Forensic software, DB Browser for SQLite, and Odin3. The method used in this study has 5 stages to carry out the forensic process, namely Preparing, Collection, Examination, Analysis, and Reporting. In the first stage, the authorities prepare equipment such as laptops and various software. In the second and third stages, the authorities used MOBILedit Forensic software, while the DB Browser for SQLite software was used in the fourth stage. From the use of MOBILedit Forensic software, important data is obtained in the form of a database with the name com.whatsapp. Furthermore, this database is analyzed using DB Browser for SQLite software. From this analysis, the bullying message is obtained in the conversation between the perpetrator and the victim. These results can then be used as digital evidence for cyberbullying cases.
References
-
[1] Mukti, W. A., Masruroh, S. U. & Khairani, D., 2017. ANALISA DAN PERBANDINGAN BUKTI FORENSIK APLIKASI MEDIA SOSIAL FACEBOOK DAN TWITTER PADA SMARTPHONE ANDROID. JURNAL TEKNIK INFORMATIKA, p. 73.
-
[2] Nasrullah, R., 2015. Media Sosial Perspektif Komunikasi, Budaya Dan Sosioteknologi. Bandung: Simbiosa Rekatama Media.
-
[3] Riadi, I., Umar, R. & Nasrulloh, I. M., 2018. ANALISIS FORENSIK DIGITAL PADA FROZEN SOLID STATE DRIVE DENGAN METODE NATIONAL INSTITUTE OF JUSTICE (NIJ). ELINVO(Electronics, Informatics, and Vocational Education), Volume 3, pp. 70-82.
-
[4] Sahu, M. S., 2014. An Analysis of WhatsApp Forensics in Android Smartphones. International Journal of Engineering Research, 3(5), pp. 349-350.
-
[5] Yadi, I. Z. & Kunang, Y. N., 2014. ANALISIS FORENSIK PADA PLATFORM ANDROID. Konferensi Nasional Ilmu Komputer (KONIK).
This page is intentionally left blank
510
Discussion and feedback