Detection of Denial of Service on Website With Wireshark Using the Anomaly-Based IDS Method
on
Jurnal Elektronik Ilmu Komputer Udayana
Volume 8, No 4. May 2020
p-ISSN: 2301-5373
e-ISSN: 2654-5101
Detection of Denial of Service on Website With Wireshark Using the Anomaly-Based IDS Method
Finandito Adhanaa1, I Ketut Gede Suhartanaa2
aInformatics Engineering, Udayana University
Unud Campus Street, Indonesia
Abstract
Denial of Service (DoS) attacks are increasingly dangerous. This DoS attack works by sending data packets continuously so that the target being attacked cannot be operated anymore. DoS attacks attack the most websites, thus making the website inaccessible. An anomaly based intrusion detection system (IDS) is a method used to detect suspicious activity in a system or network on the basis of anomaly pattern arising from such interference. Wireshark is software used to analyze network traffic packets that have various kinds of tools for network professionals.
Keywords: Denial of Service, Wireshark, Intrusion Detection System, Website, Network Traffic
The use of websites now has a very rapid development. All fields that help in every aspect of life almost 90 percent certainly have a website, such as hospitality, government, military, and others. The use of websites in these fields is inevitable and has become a major need to support their activities.
Over time, the development of technology is increasingly rapid and the crackers are even more aggressive in launching various attacks on many websites where DoS attacks are the most common type of attacks launched by crackers. This DoS attack can cause several negative impacts for the website including abnormal network communication where there is no reply to the packet in the data exchange process, shutting down the work of the website, and even worse if the target is the server is able to cause damage to the server . Based on the above problems the authors conducted a study with the title "Detection of DoS Attacks on the Website With Wireshark Using Anomaly-Based IDS Methods".
The tools used in this study are Wireshark. Wireshark is software used to analyze computer networks, where these tools are also very useful for professionals working in the field of networking, academics, and even beginners who want to learn to use and know computer network analysis. Wireshark can capture packets that run on a network. Not infrequently also information - very important information such as passwords from a social media account can be captured easily.
Anomaly-Based IDS (Intrusion Detection System) is a network security system that functions to detect interference on a computer network by detecting interference based on anomalous patterns that are caused. Denial of Service (DoS) is an example of a type of attack that damages network infrastructure, DoS attacks themselves have a unique pattern, that is, every time an attack is carried out, a continuous packet of data is sent to its target.
With the Anomaly-Based IDS method, DoS attacks can be detected by identifying the anomalous patterns that are generated. Although the error rate of the Anomaly-Based IDS method is quite large, it can detect new types of attacks.
Website security is any action or application taken to ensure website data is not exposed to cybercriminals or to prevent exploitation of websites in anyway. There are many examples of attacks on a website such as DoS (Denial of Service), Spoofing, Clickjacking, etc.
Adhana and Suhartana
Detection of Denial of Service on Website
With Wireshark Using the Anomaly-Based IDS Method DoS (Denial of Service) attack is a cyber-attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting service of a host connected to the internet.
Wireshark is a software that have purpose to analyze the computer network traffic which has very useful functions for network professionals, network administrators, researchers, and software developer [1].
The impact of a DDOS attack will cause bandwidth used by the victim will be exhausted resulting in a disconnection between servers, If DDOS attacks are not dealt with immediately they can cause damage permanent against the victim's hardware and software [2].
IDs can inspect inbound and outbound traffic in a system or network, conduct analysis, and look for evidence of intrusion attempts [3].
Security of computer networks as part of an information system is very important to maintain data validity and integrity as well guarantee the availability of services for users. A network is designed as communication data highway with the aim of increasing access to computer system, while security is designed to control access. Network supply security is a balancing act between open access with security.
According to a security expert, security computer or computer security covers some aspects such as [4] :
The privacy aspect is related to confidentiality of information. The main aspect of privacy is how to protect information from people who have no right to access.
This aspect is related to wholeness information. The main point of the integrity aspect is how information should not be changed without permission information owner.
The authentication aspect is related to identity or identity or ownership The system must know that a information created or accessed by the owner who legitimate.
The availability aspect is related to information availability.
Attack against security or security attack is all of intrusion form against information system security. There are some possibility of attack against security aspect such as [4] :
This type of attack is aimed at availability (aspect availability) of information. System can be damaged, both software and hardware, in such a way that information cannot accessed again.
This type of attack is aimed at aspects privacy and authentication. Parties who do not authorized to access information.
This type of attack is aimed at aspects privacy, authentication, and integrity not authorized to access and change information.
This type of attack is aimed at aspects privacy, authentication, and integrity is not authorized to insert fake objects into in systems such as computer networks.
There are some type of computer attack such as :
Read the package when the package on the way is called with packet sniffing this is a way attacker get existing information in the package.
System exploits which aims to make the target hang / down by sending ICMP / Ping packets with a large size that causes network performance decreases.
An attack which is done individually using one computer machine. This attack is carried out the attacker computer is stronger than the target, so the attacker is able flooding the target with packages he sent.
IDS (Intrusion Detection System) is a software application system or hardware that can detect activity suspicious in a system or network. IDS is used to detect activity suspicious in a system or network [6]. There are three type of IDS, such as :
This method is done by comparing signature of each packet to identify possible intrusion. This method is effective when IDS detects known threats, but it is not effective if the threat is new or not known by IDS.
This method is used by comparing activities are being monitored with activities that are considered normal to detect any deviations. In this method, IDS has profile that represents normal behavior from user, host, network connection and application. Profile these are obtained from the results of monitoring characteristics of an activity in an interval of time certain. The advantages of this method are effective in detecting unknown threats, for example when a network is attacked by an intrusion type the new one.
This method actually resembles anomaly-based, that is comparing existing profiles with ongoing activities for identify irregularities. However, no like anomaly-based detection which is using the host profile, stateful protocol analysis use a broader profile that can detailing how a protocol is special can be used or not. Meaning stateful here is a system in this IDS that you can understand and track the situation on the network protocol, transport and application.
In this research, we use one attacking tools and one packet analyzer. There are :
Slowloris is a type of denial of service attack tool invented by Robert "RSnake" Hansen which allows a single machine to take down another machine's web server with minimal bandwidth and side effects on unrelated services and ports. Slowloris tries to keep many connections to the target web server open and hold them open as long as possible. It accomplishes this by opening connections to the target web server and sending a partial request. Periodically, it will send subsequent HTTP headers, adding to—but never completing—the request. Affected servers will keep these connections open, filling their maximum concurrent connection pool, eventually denying additional connection attempts from clients.
Wireshark is one of many Network Analyzer tools used by network administrators for analyze network performance including protocol inside it. Wireshark is much liked because the interface that uses Graphical Users Interface (GUI) or graphical display. Wireshark able to capture packets of data or information that passes through the network. all kinds of information packages in various protocol formats too will be with easily captured and analyzed.
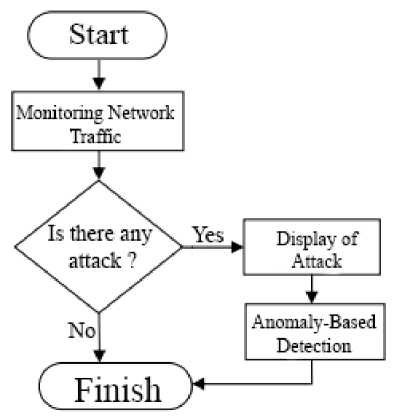
Figure 1. Research Flowchart
For the explanation of the stages of the anomaly detection process is as the following:
-
1. The initial process is the system will catch and record any data communication in and out of each network.
-
2. Any information obtained will be seen on the list in the application Whether an attack has
occurred or not.
-
3. If "Yes" there is an attack it will be carried out anomaly detection and complete, if "No"
detection will be finished.
This research was completed by using the order method as the following:
-
1. Literature Study
Gather data or information from various sources such as books and searches data via the internet.
-
2. Literature Study
Study related information with computer networks, anomaly-based methods, and all relate matters with the network model.
-
3. Trial and Evaluation
At this stage a network trial is conducted to look for problems that might arise, and evaluate.
Implementation of attack detection systems computer network using the method anomaly-based, then the application is installed Wireshark on a computer that uses a system Mac OS operations, for monitoring network. For DoS attacks, the Slowloris application is used. The IP of the attack sender is 192.168.1.6 and the target itself is a website that is pudihomestay.com with an IP address of 156.67.212.136. Time for testing phase in this research is 10 minutes.
The testing phase is divided into two, namely when the attack has not been carried out and when the attack has been done.
With an estimated time of 10 minutes, there are 1447 network traffic, and in the source and destination tables on figure 2., there is no packet sending from 192.168.1.6 to the destination that is 156.67.212.136. The packet sending phase indicate that the DoS attack from attackers to the destination, which is the website, pudihomestay.com.
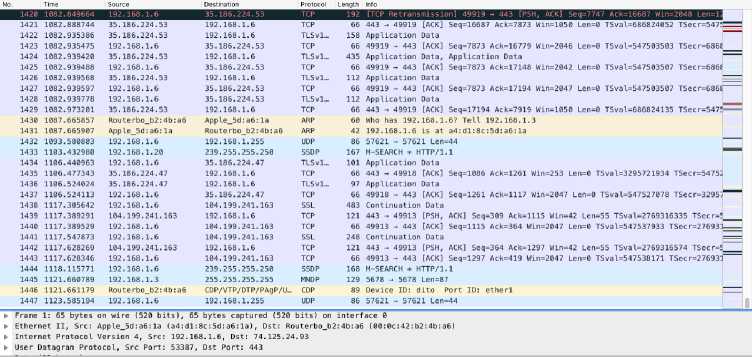
Figure 2.Wireshark Intercept The Condition of Network Without DoS Attack Anomaly
In this phase, launch the Slowloris application to send the DoS attack to the destination, pudihomestay.com that is shown on figure 3.
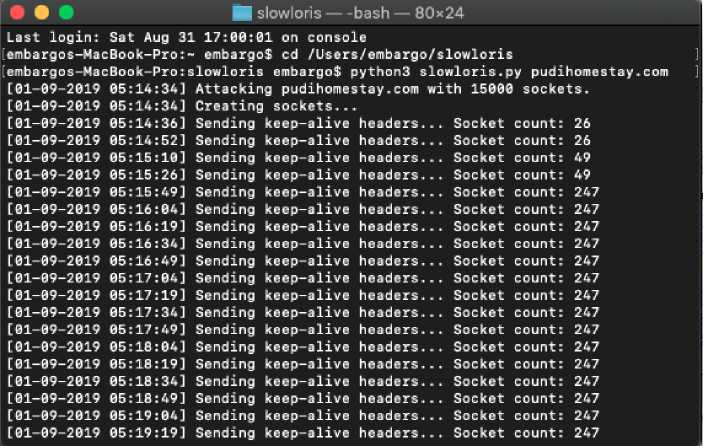
Figure 3.Launching The Slowloris
After launch the attack to the destination, Launch the Wireshark to analyze the network traffic. And the result is shown on figure 4.
69837
69838
69839
515.234734 515∙240061
515.246673
192.168.
74.125.12.168
69841
69842
69843
69844
69845
69846
69847
69848
515.249453
515.255191
515.264418
515.267624
515.271757
515.277070
515.277189
515.287440
515.288247
192.168.1.6
192.168.1.6
74.125.12.168
UDP
UDP
80
1392
58426
443 -
192.168.1.6
74.125.12.168
74.125.12.168
74.125.12.168
192.168.1.6
192.168.1.6
192.168.1.6
74.125.12.168
192.168.1.6
192.168.1.6
192.168.1.6 74.125.12.168
443 - 58426 Len=1350
69850
69851
69852
69853
69854
69855
69856
69857
515.293628
192.168.1.6
UDP UDP UDP UDP UOP UOP UDP
1392
76
1392
1392
1392
515.297684
515.304803
515.310173
515.314590
515.315477
515.320746
515.324818
515.328205
192.168.1.6
74.125.12.168
74.125.12.168
192.168.1.6
74.125.12.168
74.125.12.168
192.168.1.6
192.168.1.6
74.125.12.168
192.168.1.6
192.168.1.6
192.168.1.6
192.168.1.6
515.328484
69860
69861
69862
69863
515.332454
515.332722
515.377250
515.381509
515.398758
69864 517.902612
192.168.1.6
192.168.1.6
UOP UDP UOP UOP UOP UDP UDP
443 -58426 443 -
443 -443 -58426 58426
443 -
1392
1392
76
1392
1392
192.168.1.6
74.125.12.168
192.168.1.20
192.168.1.6
74.125.12.168
192.168.1.6
239.255.255.250
UDP UDP UDP UOP
91
63
1392
SSDP
58426 Len=1350 - 443 Len=34
58426 Len=135B
58426 Len=1350
58426 Len=1350
58426 Lβn=1350
58426 443 -
443 -58426 443 -443 -58426
443 -
58426 L4Aal350
- 443 Len=34 58426 Len=1350 58426 Len=1350
58426 Len=1350
58426 Len=1350
58426
443 -
443 -58426
58426 Len=883
167 M-SEARCH
- 443 Len=49 58426 Len=21 58426 Len=1350 - 443 Len=29
FlilitrtTH
► Frame 69864: 167 bytes on wire (1336 bits). 167 bytes captured (1336 bits) on interface 0
► Ethernet II, Src: SamsungE-32:05:0c (20:5e:f7:32:05:0c), Ost: IPv⅛acast-7f:ff:fa <01:08:5e:7f:ff: fa)
k Internet Protocol Version 4, Src: 192.168.1.20, Ost: 239.255.255.250
-
► User Datagram Protocol, Src Port; 3S0W. Dst Port; 1980______________________________________________
Figure 4.Network Analyzer Result With DoS Attack Using Slowloris
From the Wireshark analyze result, from 10 minutes time of testing phase, the total of network traffic is 69864. And there is package sent continuously from attacker with IP address 192.168.1.6 to the destination, pudihomestay.com, with IP address 156.67.212.136, which is shown on Figure 5.
|
o. Time Source Destination Protocol Length Info 59748 453.018735 192.168.1.6 156.67.212.136 TCP 65 50160 → 59749 453.018755 192.168.1.6 156.67.212.136 TCP 65 50161 → 59750 453.018775 192.168.1.6 156.67.212.136 TCP 65 50162 → 59751 453.018795 192.168.1.6 156.67.212.136 TCP 65 50163 → 59752 453.018815 192.168.1.6 156.67.212.136 TCP 65 50164 → 59753 453.018835 192.168.1.6 156.67.212.136 TCP 65 50165 → 59754 453.018855 192.168.1.6 156.67.212.136 TCP 65 50167 → 59755 453.018876 192.168.1.6 156.67.212.136 TCP 65 50168 → 59756 453.018896 192.168.1.6 156.67.212.136 TCP 65 50169 - 59757 453.018917 192.168.1.6 156.67.212.136 TCP 65 50170 → 59758 453.018937 192.168.1.6 156.67.212.136 TCP 65 50171 - 59759 453.018958 192.168.1.6 156.67.212.136 TCP 65 50173 → 59760 453.018978 192.168.1.6 156.67.212.136 TCP 65 50174 → 59761 453.018998 192.168.1.6 156.67.212.136 TCP 65 50175 → 59762 453.019018 192.168.1.6 156.67.212.136 TCP 64 50176 → 59763 453.019038 192.168.1.6 156.67.212.136 TCP 65 50177 → 59764 453.019058 192.168.1.6 156.67.212.136 TCP 65 50178 → 59765 453.019078 192.168.1.6 156.67.212.136 TCP 65 50179 → 59766 453.019101 192.168.1.6 156.67.212.136 TCP 65 50180 → |
I | ||
|
► Frame 69864: 167 bytes on wire (1336 bits), 167 bytes captured (1336 bits) on interface 0 ► Ethernet II, Src: SamsungE_32:05:0c (20:5e:T7:32:05:0c), Dst: IPv4mcast_7f:ff:fa (0l:00:5e:71 ► Internet Protocol Version 4, Src: 192.168.1.20, Dst: 239.255.255.250 | |||
Figure 5.DoS Attack Detected Using Wireshark
In carrying out some of these tests above, the advantages of Wireshark can detect attacks carried out by intruders by looking information from the results of data packet capture done, from the start of the IP used attacker, and what protocol is used. Lack of this product can’t prevent attacks that occur, but can only monitor suspected data packets as intruders who carry out attacks on computer network.
And with those two type of testing phase, we can conclude that DoS attack can cause of massive traffic of data. And those massive traffic of data can cause of bad service in website service.
-
a. Wireshark can be used well by applying anomaly-based methods IDS.
-
b. Security of data or information on a computer security can be guaranteed from intruder attack. By knowing from data packets captured by Wireshark, and analyze each of these packages.
References
-
[1] M. Junaidi Putra, Ilham Faisal, S.T, M.Kom, and Arief Budiman, S.T, M.Kom, "Deteksi Serangan Pada Jaringan Komputer Dengan Wireshark Menggunakan Metode Anomally-Based IDS" STTH Medan, vol. 1375, Page Number, 2017.
-
[2] Rudi Hermawan, "Analisis Konsep Dan Cara Kerja Serangan Komputer Distributed Denial of Service" Unindra, vol.5, Page Number, 2015.
-
[3] Khairil, Toibah Umi Kalsum, "Implementasi Intrusion Detection System Sebagai Keamanan Website Server Universitas Dehasen Bengkulu" Jurnal Pseudocode, vol. 1, Page Number 1, 2014.
-
[4] Iwan Sofana, Membangun Jaringan Komputer, 1 Edition., Bandung: Informatika, 2008.
-
[5] Dony Ariyus, Intrusion Detection System, 1 Edition., Yogyakarta: Andi, 2007.
-
[6] Jutono Gondohanindijo, Sistem Untuk Mendeteksi Adanya Penyusup (IDS : Intrusion Detection System), 1 Edition., Semarang:Universitas AKI, 2011.
380
Discussion and feedback