digiSCAN: A Supermarket Anti-Theft Scanner
on
Journal of Electrical, Electronics and Informatics, Vol. 6 No. 1, February 2022
10
digiSCAN: A Supermarket Anti-Theft Scanner
Benjamin Kommey1, Elvis Tamakloe2
Kwame Nkrumah University of Science and Technology, KNUST
Department of Computer Engineering
Faculty of Electrical and Computer Engiineering
College of Engineering
Kumasi - Ghana
Abstract Supermarket shopping is an essential part of the livelihood of most people around the world. Consumers can acquire items essential for their daily activities. However, in an ever-evolving world with an increasing population and increasing crime rates, supermarket theft is becoming a prevalent problem with supermarket owners spending large sums of money on hiring security often with little effect. Organized Retail Crime ORC) costs the retail industry approximately $30 billion each year, with 71.3% of retailers reporting an increase in ORC year-over-year. With the current global economic conditions, high labor costs are longer feasible. Consumers also face the issue of paying for items they did not select. Advanced camera systems, for some, may be an escape however, this approach is not feasible for all aspects of shopping and in underdeveloped countries that have technical constraints. The advent of digitization has helped improve the livelihood of consumers in Ghana. Currently, many large-scale retailers are oblivious to some of these advancements. The oblivion of the management of such retail services results in the loss of products, customer dissatisfaction and the mismanagement of untracked products by employees. To reduce theft and the mismanagement of products by employees, a smart antitheft system should be deployed in supermarkets; at the till and before the exit of supermarkets to ensure all products leaving the store are paid for and accounted for. The system consists of a deactivation and theft detection system. The product is deactivated by the store attendant at the till when the customer pays for the product. However, if a customer crosses the initial warning zone without paying, a warning sound is triggered and after the customer crosses the final warning zone, the alarm is triggered indicating an attempted theft by the customer. A log of products is also kept ensuring employees are not stealing products. This paper presents a smart way of detecting theft during supermarket shopping using Radio Frequency Identification RFID) readers and tags, microcontroller-based control system, a database server and an Integromat.
Index Terms— Antitheft, Embedded systems, RFID, Supermarket.
-
I. INTRODUCTION1
In industrial warehouses, retail and shopping centers, variety of monitoring, detection and control mechanisms have been implemented to check shrinkage. The use of barcodes, quick response codes among other anti-theft detection methods have provided some success but leaves much to be desired.
The emergence of radio frequency identification RFID) technology has imperatively redefined several facets of our everyday life. This type of automatic identification and data capture AIDC) technology involves the assignment of special identifier to product and has contributed immensely to the area of wireless communication, monitoring, tracking and control applications. RFID technology primarily employs electromagnetic fields to detect, identify and track tagged objects. It essentially consists of an RFID reader which collects radio waves from an RFID tag and converts them into data which can be relayed to a host computer
through a communication interface with the aid of an antenna. Based on their mode of operation data collection), an RFID reader can be fixed or mobile. RFID transponder tags on the other hand are made of very small integrated circuits IC) which incorporates a radio transmitter and receiver. It essentially transmits data to an RFID reader when activated by an electromagnetic interrogation pulse from a reader in proximity. RFID tags are categorized into either passive tags or active tags based on their design. Active tags in their design have an onboard power supply unit to always ensure effective transmission of data. Unlike active tags, passive tags are powered by the RFID reader to enable data transmission. This feature makes them less expensive to design and develop. Thus, passive RFID tags are predominantly used. RFID technology does not need direct line of sight for its operation.
To reduce or eliminate shrinkage and boost revenue in business centers, RFID technology can be optimized with internet of things IoT). This paper presents a smart antitheft scanning system digiSCAN) which applies spreadsheet applications like Microsoft excel and google sheets. The Microsoft excel features a calculation, graphing
tools and a macro programming language called Visual Basic for Applications VBA). Google sheets are compatible with Microsoft excel file formats and therefore allows users to create and edit files online while collaborating with other users in real-time. Thus, users can track edits with a revision history.
-
II. RELATED WORKS
The increase spate of theft cases recorded daily in supermarkets and malls have led to the development of stringent mechanisms aimed at tackling this menace head-on. Besides the enactment of strict laws to curtail this situation, technological advancements have provided a few innovative solutions to this problem with different developed models.
A few models have been proposed to aid theft detection by scanning barcode of products [1][2]. In [1], a model was designed for shoppers to self-scan products using barcode scanners. This model primarily employs a barcode reader, microcontroller, liquid crystal display LCD) and oscillator. A barcode reader is used to read and decode the unique identity ID) of the product. The decoded data is delivered to a microcontroller for instant processing and billing. The purchased products and bills are displayed on an LCD for the shopper. Although this system facilitates faster payment of products which reduces congestion at the payment terminals, manual inspection of shoppers by security is required to determine whether an item stolen by a shopper has been accounted for enroute to exit the supermarket. Hence, automatic detection of stolen products is impossible with this system.
[3-5] proposed an anti-theft detection system using quick response QR) code scanners. Unlike barcode scanning which requires LED or laser lights for operation, QR code scanners are dependent on camera-based scanning technology. Regarding the model in [4], an advanced shopping trolley was designed based on QR code. A QR code scanner is used to capture and decode the product ID. This information is sent to a microcontroller where it is processed, stored, and displayed on an LCD. This data is simultaneously transferred to a payment terminal computer via ZigBee. Even though this system is user friendly and provides shoppers with convenience at payment terminals, manual inspection is needed to assist with theft detection which can be laborious and ineffective. Additionally, QR codes cannot be provided on all products. Thus, are product biased or selective.
A few works have presented variety of designs that uses anti-theft radio frequency identification RFID) technology [6-11]. Some of these models have incorporated different communication modules to their system [12-15]. In reference to the model proposed in [8], the system incorporates an RFID reader, LCD and ZigBee transceiver mounted on a cart. The RFID reader with the help of a passive RFID tag scans and tracks the purchased product. Information and bill of the purchased product is recorded and displayed on an LCD. The ZigBee transceiver communicates with a centralized server to recommend and provide online transaction. More so, an RFID reader at the
exit door detects theft of unpurchased products. This proposed model enhances customers shopping experience, prevents shrinkage and reduces labour cost. However, it is capital intensive and requires routine checks.
Closed circuit television CCTV) cameras have experienced a fair share regarding theft surveillance in supermarkets [16-19]. The model showcased in [16] offers the monitoring and detection of theft behaviors using high definition HD) cameras in combination with convolutional neural network CNN). This system employs an HD camera mounted at vantage points in the supermarket to monitor the customer. Real time data of the customer’s behavior is recorded, transmitted, and collected onto a personal computer PC). Based on recognition models or algorithms trained using CNN, the PC identifies theft actions and subsequently sets off an alarm. This system provides fast response, high recognition accuracy, enables modification and addition of new data sets and reduces labour cost. Despite these benefits, this model requires intensive programming and experts for routine maintenance and upgrades. Hence can be capital intensive.
Alternatively, there are theft detection systems based on infrared technology [20-23]. [21] suggested a model that incorporates pyroelectric infrared PIR) sensor with a microcontroller and a global system for mobile communication GSM) module. The PIR sensor senses and forwards logic signals to the microcontroller upon detection of objects in proximity. This information is processed by the microcontroller which subsequently activates a GSM module to trigger an alert via call or short message service SMS) to a corresponding GSM mobile phone number. Though this system provides a high level of security against theft, it is only applicable to certain products in the supermarket.
-
[24] proposed a smart IoT surveillance system which utilized a gyroscope to detect angular disturbances of doors in shopping centers. Heavy disturbances such as knocking or cutting of the door is detected by a MEM sensor, processed by a microcontroller and as per the programming algorithm, an alert system is triggered. Even though this system detects grand theft in supermarkets, it cannot detect theft of products under normal shopping conditions. Hence requires additional anti-theft mechanisms.
III. METHODS AND PROCEDURES
A. DigiSCAN System Architecture

Fig. 1. DigiSCAN System Architecture
Figure 1 shows the digiSCAN system architecture consisting mainly of three 3) zones i.e., Free zone FZ, Deactivation zone DZ and Warning and Theft Detection zone TDZ. A customer after shopping in the free zone, moves to the deactivation zone and would be attended to by waitress, sales cashiers, or shop attendants. The tag on the item is then deactivated when the customer pays for the item at the till of the store. The store computer has a bespoke software which facilitates the billing process. A warning sound is sounded when the customer crosses the yellow zone in the Warning and Theft Detection zone to alert the customer to pay for an item, he or she may have forgotten to pay for or otherwise. If the customer ignores the warning and continues to cross the red zone, security is alerted and an alarm is sounded to indicate theft attempted by the customer.
C. digiSCAN System Deactivation Flow Chart
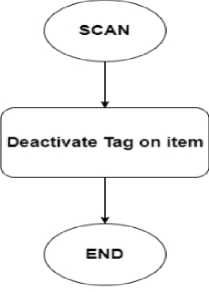
Fig. 4. digiSCAN System Deactivation Flow Chart
-
B. digiSCAN System Block Diagrams
The digiSCAN system consists of an embedded hardware and software application. The embedded hardware has three
-
3) main blocks namely: The Deactivation block DB, the Warning block WB and the Theft Detection block TDB.
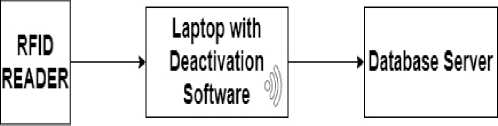
Fig. 2. digiSCAN Deactivation Block
Deactivation Block DB: As shown in Figure 2, in the DB, the RFID reader deactivates the active tag on product taken and updates the centralized database through the on-board Wi-fi system.
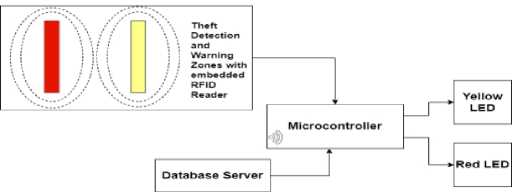
Fig. 3. digiSCAN Warning and Theft Detection Block
Warning WB and Theft Detection Block TDB: Figure 3 illustrates the WB and TDB, where initially, the database will compare the status of the product at the warning zone and the information in the database. If the customer is in the yellow zone, a warning is triggered to alert the customer to go back and deactivate any active tags he or she may have. If the customer ignores this and proceeds to move on to the red zone, security is alerted, and an alarm is sounded.
The digiSCAN software application can be installed on any desktop or laptop which will serve as the store computer for product deactivation and for the warning and theft detection alarm system which are the spreadsheet applications Microsoft Excel and Google Sheets) with Integromat integration for live communication and update of tag status.
Deactivation System
When the items are scanned, the RFID Reader reads the tag, then the microcontroller updates the database server to indicate a tag has been deactivated.
D. digiSCAN System Warning and Theft Detection Flow Chart
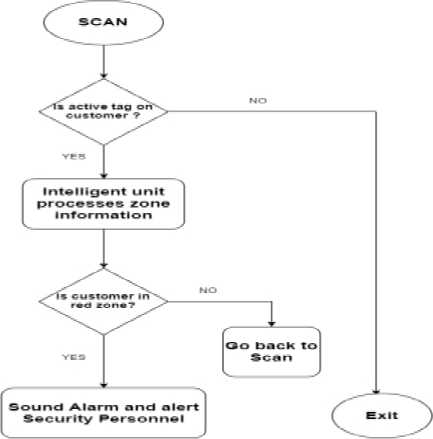
Fig. 5. digiSCAN System Warning and Theft Detection Flow Chart
Warning and Theft Detection System
When the items are placed into the cart, the RFID Reader reads the tag, and the microcontroller updates the database server to indicate an item was picked.
-
IV. RESULTS
A. System Setup
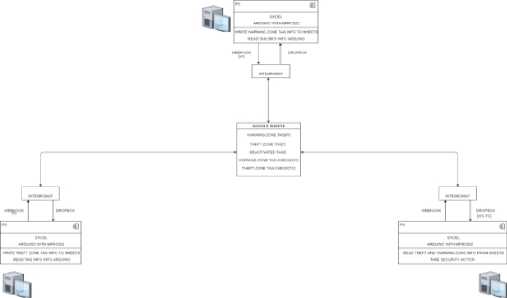
Fig. 6. digiSCAN System Test Overview
As depicted in Figure 6, the digiSCAN system setup used for testing consists of four functional units: the deactivation unit, warning zone unit, the theft detection unit, and the security unit. It was ensured that the various units and software API, in this case Google Sheets, Warning Zone Excel sheet and Theft Detection Unit used are synchronized using the Integromat API. Active connections are established at the Warning and Theft Detection Units to facilitate this process.
Once the information from the two units is fed into
Google Sheets, a VLOOKUP is made to check if the incoming tag has been deactivated or not. The state of this lookup is then written into the Security Unit. Table 1 contains the various unit tests and outcomes.
Table 1 digiSCAN Unit Test Outcomes
|
Unit |
Outcome |
|
Deactivation Unit |
All deactivated tags from checkout are sent to a given column on Google Sheets. |
|
Warning Zone Unit |
The Data Streamer functionality of Excel is used to communicate serially with an Arduino board connected to this unit. Through Excel and Visual Basic, tags that are read are sent to a third-party API, namely Integromat, to handle syncing between Excel and Sheets. This allows for real-time communication between tags read in the warning zone and Google Sheets. |
|
Theft Detection Unit |
Similar to the Warning Zone Unit, the Data Streamer functionality of Excel is used to communicate serially with an Arduino board connected to this unit. Through Excel and Visual Basic, tags that are read are sent to a third-party API, namely Integromat, to handle syncing between Excel and Sheets. This allows for real-time interaction between tags read in the theft detection zone and Sheets. |
|
Security Unit |
Information processed from the Warning Zone Unit and the Theft Detection Units are sent as Boolean values into the Security Unit in the form of a tuple as (ZONE, STATUS . Based on the state of the operation and the zone, the appropriate buzzer is sounded to alert authorities of an ongoing theft or of a successful transaction. |
The digiSCAN embedded hardware was tested using the Arduino Uno board for the Theft Detection Zone and
Warning Zone units. An Arduino Mega board was used in the implementation of the Security Unit. Other components used in the digiSCAN setup are MFRC522, breadboard, LEDs, and buzzers as well as useful Arduino libraries and headers. Figure 7 shows the hardware components and Table 2 contains some digiSCAN software application sample codes used to read and pass the values of the RFID into the sheets google and excel) in hexadecimal values.
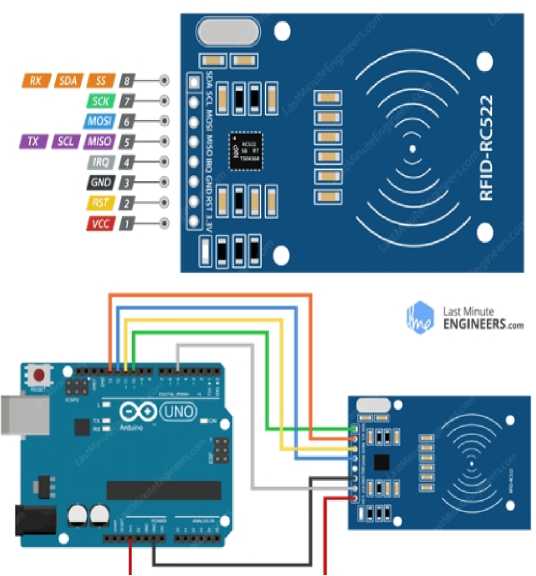
Fig. 7. digiSCAN Test Hardware Components
Table 2 digiSCAN Software Application Sample Codes
-
j) include <SH . h> •include <MmC52t«h>
•define 55.PIN 10
•define RST-PIN 9
MFRC522 rfld(SS_PIN, RST_PIN): ∕∕ Instance of the class
MFRC522:IMIFAPE Key key:
∕∕ Inlt array that will store new NUID byte nuidPICC(4];
void setup() (
Serial.begin(XQO) ; SPI.begin(): ∕∕ Inlt SPI bus xfld.PCD-Inlt(); ∕∕ Inlt MFRC522
for <byte 1-0: 1 < 4; 1++) ( key.keyByte[1] - OxFF:
Integromat, a third-party API was used for the automation and synchronization between the individual units. Figure 9 shows some scenarios applied for active connection during testing.
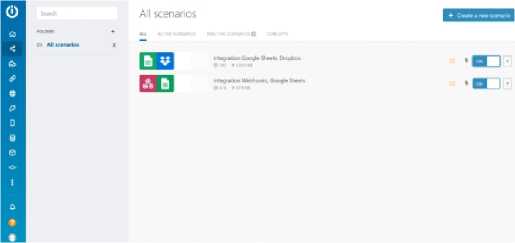
Fig. 9. digiSCAN Test Scenarios
Using Visual Basic, an active GET is created to Integromat as a listening event. Once it detects a change which represents a card has been read), it sends an instant acknowledgment to Integromat with an update of the card value being made on Google Sheets. Figure 10 depicts the Microsoft VBA macro in action and Table 3 contains a few macro functions applied for this test and the expected results.
The RC522 module data transfer code snippet is as shown in Figure 8. The sample code also shows how the warning and theft detection zones work with the buzzer and LEDs to warn customers or indicate theft.
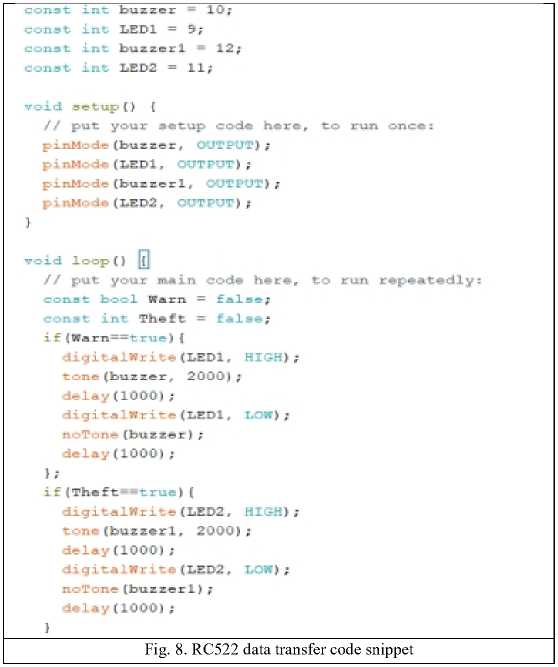

Fig. 10. digiSCAN VBA macros
Table 3 digiSCAN VBA macros
|
Macro |
Function |
|
='Data In’! B22 |
Sheet linking between Arduino serial input and synchronized sheet on Excel for Google Sheets |
|
=IF (ISERROR (VLOOKUP (A1, $B$1001,1, FALSE , FALSE, TRUE |
Performing VLOOKUP to check if a given RFID tag has already been accounted for. The output of this lookup is fed together with the current zone into the Arduino Mega for the Security Unit to process. |
Other Approaches Considered during testing are:
-
• Using Radio Frequency to generate metallic resonance.
-
• Use of OneDrive instead of Integromat for synchronization.
Using the theft case scenarios, five 5) out of the six 6) tags were detected and recorded accordingly. This indicates an 83.3% efficiency for the digiSCAN system implementation. The Warning and Theft Detection Zones also work well independently of each other with no false alarms or false positives. The reading range of the MFRC522 however, was very short with a range of < 5cm.
-
V. CONCLUSION
Based on the testing and evaluation of the system, the Supermarket Antitheft Scanner System was successful in detecting and eliminating theft. The spreadsheet application integration Google Sheets and Microsoft Excel) helps keep inventory of store items. The system is also highly scalable. Further improvements to the system could be embedding of product information into tags for product identification, a police alert through an SMS alongside the Warning Zone alarm and the use of a different database system such as Mongo DB instead of Google Sheets for very large-scale applications. UHF RFID readers can also be used with this implementation to increase range of reading.
REFERENCES
-
[1] Megha R. Mane, Nilam G. Amane, Sunita D. Patil and Archana L. Lakesar, “Electronic Shopping Using Barcode,” International Research Journal of Engineering and Technology, vol. 3, Issue 04, 2016, ISSN: 2395-0056.
-
[2] Mohammed Ghazal, Maha Yaghi, Abdalla Gad, Gasm El Bary, Marah Alhalabi, Mohammad Alkhedher and Ayman S. El-Baz, “AI-Powered Service Robotics for Independent Shopping Experiences by Elderly and Disabled People,” Applied Sciences, 2021, 11, 9007, https://doi.org/10.3390/app1199007.
-
[3] Chwei-Shyong Tsai, Hsin-Liang Chen, Hsien-Chu Wu, and Josh Jia-Ching Ying, “A Puzzle-Based Data Sharing Approach with Cheating Prevention Using QR Code,” Symmetry, 2021, 13, 1896, https://doi.org/10.3390/sym13101896.
-
[4] S. R. Patil, Ginni Chaddha, Anjali Singh and Komal Kant, “Design of Advanced Shopping Trolley based on QR Code,” International Journal of Engineering Research and Technology, Vol. 5, Issue 03, 2016, ISSN: 2278-0181.
-
[5] M. S. Siva Priya, Jatin Agrawal, Debayan Roy and Rajkumar Chirra, “Easy Payout, Advanced shopping, and Security in Super Market,” International Journal of Innovative Technology and Exploring Engineering, Vol. 8, Issue-12, 2019, ISSN: 2278-3075.
-
[6] Ademola Abdulkareem, Awosope C.O.A and Tope-Ojo A.E, “Development and Implementation of a miniature RFID system in a shopping mall environment.” International Journal of Electrical and Computer Engineering, Vol. 9, No. 2, 2019, pp. 1374-1378, ISSN: 2088-8708, doi: 10.11591/ijece.v9i2.pp1374-1378.
-
[7] Ghaith Khalil, Robin Doss and Morshed Chowdhury, “A New Secure RFID Anti-Counterfeiting and Anti-Theft Scheme for Merchandise,” Journal of Sensor and Actuator Networks, 2020, 9, 16, doi: 10.3390/jsan9010016.
-
[8] Ankush Yewatkar, Faiz Inamdar, Raj Singh, Ayushya and Amol Bandal, “Smart Cart with Automatic Billing, Product Information, Product Recommendation Using RFID and Zigbee with Anti-Theft,” 7th International Conference on Communication, Computing and Virtualization, 2016, pp. 793-800, doi: 10.1016/j.procs.2016.03.107.
-
[9] Yerlan Berdaliyev, and Alex Pappachen James, “RFID-Cloud smart cart system,” 2016 International Conference on Advances in Computing, Communications and Informatics (ICACCI , 2016, pp. 2346-2352, doi: 10.1109/ICACCI.2016.7732405.
-
[10] Amani Nasser Said Al Julandani, Ferddie Quiroz Canlas, and Sarachandran Nair, "“Do It Yourself” Product Scanning System for Supermarket Customers with Anti-Theft Feature: A Proposed Model," 2020 International Conference on Computing, Networking, Telecommunications and Engineering Sciences Applications (CoNTESA , 2020, pp. 40-44, doi:
10.1109/CoNTESA50436.2020.9302861.
-
[11] Ng Xin Jie and Intan Farahana Binti Kamsin, “Self-Checkout Service with RFID Technology in Supermarket,” Proceedings of the 3rd International Conference on Integrated Intelligent Computing, Communication and Security (ICIIC , Atlantis Highlights in Computer Sciences, Vol.4, pp. 495-502,2021.
-
[12] Hasan Al-Sakran, “Agent and Radio Frequency Identification Based Architecture for Supermarket Information System,” Journal of Computer Science 9 (6 , pp. 699-707, 2013, ISSN: 1549-3636, doi: 10.3844/jcssp.2013.699.707.
-
[13] Mobeen Shahroz, Muhammad Faheem Mushtaq, Maqsood Ahmad, Saleem Ullah, Arif Mehmood and Gyu Sang Choi, “IoT-Based Smart Shopping Cart Using RFID Frequency Identification,” IEEE Access, vol. 8, pp. 68426-68438, 2020, doi: 10.1109/ACCESS.2020.2986681.
-
[14] B. Karunakara Rai, J.P. Harshitha, Radhika S. Kalagudi, B.S. Priyanka Chowdary, Palak Hora and B. Sahana, “A Cloud-Based Inventory Management System Using a Smart Trolley for Automated Billing and Theft Detection,” Springer Nature Singapore, 2019, https://doi.org/10.1007/978-981-13-3765-9_51.
-
[15] Rajlakshmi Badi and Bashirahamad Momin, “SCAR: Smart Cart based on ARM algorithm and RFID technology,” 2018 3rd IEEE International Conference on Recent Trends in Electronics, Information and Communication Technology (RTEICT , 2018, pp. 2387-2392, doi: 10.1109/RTEICT42901.2018.9012562.
-
[16] Y. Zhang, S. Jin, Y. Wu, T. Zhao, Y. Yan, Z. Li and Y. Li, “A NEW INTELLIGENT SUPERMARKET SECURITY SYSTEM,” Neural Network World 2, pp. 113-131, 2020, doi:
10.14311/NNW.2020.30.009.
-
[17] Santosh Mahale, Shivam Gujrathi, Pratik Bramhecha, Kalyani Bedarkar, Rohini Shinde and Yashraj Patil, “Survey on Anti-Theft Detection System,” International Journal of Innovative Research in Science, Engineering and Technology (IJIRSET , Vol. 9, Issue-4, 2020, e-ISSN: 2319-8753.
-
[18] Yoji Yamato, Yoshifumi Fukumoto and Hiroki Kumazaki, “Security Camera Movie and ERP Data Matching System to Prevent Theft,” 2017, https://arxiv.org/pdf/1706.04595.
-
[19] Mandar Shriram Munagekar, “Smart Surveillance system for theft detection using image processing,” International Research Journal of Engineering and Technology (IRJET , Vol. 05, Issue 08, 2018, e-ISSN: 2395-0056.
-
[20] Prithvi Nath Saranu, G. Abirami, S. Sivakumar, M. RameshKumar, U. Arul and J. Seetha, “Theft Detection System using PIR Sensor,” 4th International Conference on Electrical Energy Systems (ICEES , pp.656-660, 2018,
https://www.academia.edu/41441856/Theft_Detection_System_usin g_PIR_Sensor.
-
[21] K.M. Ramesh Kumar, R. Venkadesh, K. Vengatesh and P. Nagaraj, “Theft Detection and Prevention Based on Internet of Things,” International Journal of Innovative Research in Science, Engineering and Technology, Vol. 7, Issue 11, 2018, ISSN(Online : 2319-8753.
-
[22] Sundar raj M, and J.S. Reshma, “Review On Infrared Theft Security Alarm,” International Journal of Pure and Applied Mathematics, Vol. 118, No. 18, 2018, pp. 625-633, ISSN(Online : 1314-3395.
-
[23] Amanda Berg, “Detection and Tracking in Thermal Infrared Imagery,” PhD dissertation, Department of Electrical Engineering, Linköping University, Linköping, Sweden, 2016, ISSN: 0280-7971, Available: http://liu.diva-
portal.org/smash/get/diva2:918038/COVER01.pdf
-
[24] Ishaan Singh Panwar, Yash Karvasra, and Harpreet Kavr Channi, “Designing of IOT Theft Notification Door,” International Journal for Scientific Research and Development, Vol. 9, Issue 7, pp. 267-274, 2021, ISSN(Online : 2321-0613.
Discussion and feedback