Ransomware Attack using AES Encryption on ECB, CBC and CFB Mode
on
Jurnal Ilmu Komputer VOL. XII No. 1
p-ISSN: 1979-5661
e-ISSN: 2622-321X
Ransomware Attack using AES Encryption on ECB, CBC and CFB Mode
Feillyan Alfreda Antariksa, Is Mardianto
Informatic Engineering, Trisakti University
Jakarta, Indonesia feillyan064001400012@std.trisakti.ac.id mardianto@trisakti.ac.id
Abstract
With the help of internet, users are faster getting data that they needed. It’s possible that villain insert an evil program (malware) without user knowing it. One of the malwares that spread like a plague right now is ransomware. The infected computer system will encrypt all files on the computer and blackmail the users to pay some money if you want to access back your files. For this experiment it’s using 2 approach, first is using online attack and second is offline attack. Ransomware in this experiment is using AES 256 for encrypting the files and using ECB, CBC and CFB mode for comparing time. As the result ECB is 39.5% faster than CBC and 7,17% faster than CFB. For CFB is 34,83% faster than CBC.
Keywords: Ransomware, Malware, AES 256, ECB, CBC, CFB
One of malware function is it can remotely control others computer to send data without user knowing it. It can use to encrypt user data an extorting for money for example [1]. In 2005 – 2006 was the first ransomware attack appear when the culprit tries to blackmail the victim with US$300. Just in 10 year on 2016, Trend Micro found 247 newly ransomware while a year ago on 2015 only 29 ransomwares can be found. Its increased 752% just in one year [2]. There are 2 types of ransomware, first one is locker ransomware that locked your computer from the user. Its objective is to limit your resources on your computer so the user only can use keyboard at numerical type so user can’t do anything except for paying them via bitcoin. Second one is the Crypto ransomware, its encrypt all the user files so the files can’t be opened anymore. When it involved precious or sensitive data, user will do anything to get that back including paying the culprit to get the decrypt key. Even more, the ransomware gave users the warning with the “time left” or “don’t turn off the internet otherwise key is disabled” something similar like those [3].
When the downloadable file is executed, the program will generate key to encrypt all the files at victim hard drive. The encrypted file cannot be open or access before the victim paying some money in cryptocurrency like Bitcoin, Redcoin, Ethereum, Litecoin etc. After the payment done, then the key to decrypt will be given as shown on Figure 1.
In offline attack, malware is inserted in flash drive. When the malware in the flash drive executed, file automatically open and the key for decrypting is created in the flash drive. File in computer will be encrypted in a specified time as shown on Figure 2.

that spread out in
IF YOU PAY
There is a chance that your file will be back
to normal
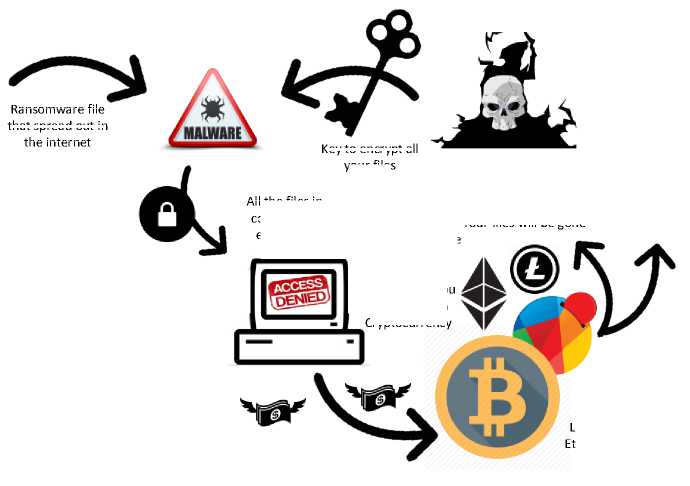
Ransomware file
the internet
Key to encrypt al
Payment using Cryptocurrency like Litecoin, Bitcoin, Redcoin, Ethereum etc. so it canʼt be track
All the files in computer is encrypted
your files
IF YOU DIDNʼT PAY y
There is a message that contain address and amount that yo need to pay in Cryptocurrency
Your files will be gone
Figure 1. Online Attack Ransomware Scheme
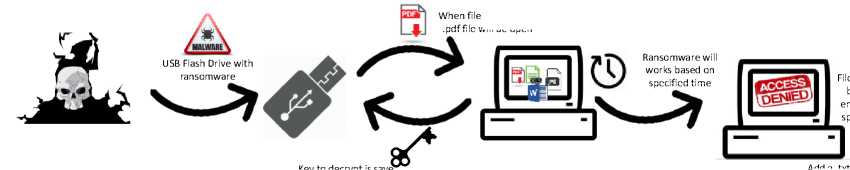
LJSB F ash Drive with
Ransomware wil
works based ππ
specified time
Key to decrypt is save in USB Flash Drive
When file is executed, pdf file will be open
File on computer will be automatically encrypted after the specified time pass
IF YOU DIDNʼT PAY
Your files will be gone
IF YOU PAY
There is a chance that your file will be back to normal
Payment using Cryptocurrency like Litecoin, Bitcoin, Redcoin, Ethereum etc. so it canʼt be track
Figure 2. Offline Attack Ransomware Scheme
Add a .txt file that contain address and amount in
Cryptocurrency
Developed by Joan Daemen and Vincent Rijmen, Advanced Encrypted Standard (AES) use a 128 bits of data block and 128, 192 or 256 bits of cipher key.[4 FIPS]. Encryption process is shown on Figure 3.
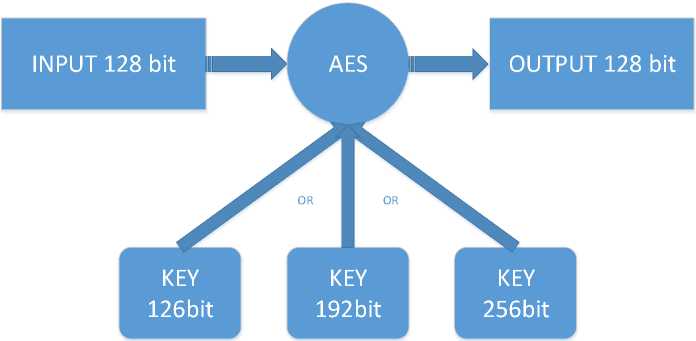
Figure 3. AES Process
AES algorithm work by repeating the same step in a certain rounds (10 round for 128 bit, 12 round for 192 bit, 14 round on 256 bit)[5 IJETT]. In this paper, AES that going to be use is AES 256 bits.
The first mode that will be used is AES ECB (Electronic Codebook). It’s most simple encryption from the other mode because each block is encrypted using the same key shown on Figure 4.
The formula used is as follow [6]:
Encryption
Decryption
Cj = CIPHK(Pj)
P1 = CIPH-1K(Cj)
ENCRYPTION
PLAINTEXT

CHIPHERTEXT
for j = 1 … n.
for j = 1 … n.
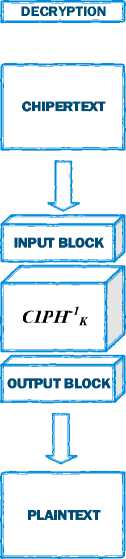
Figure 4. AES ECB mode
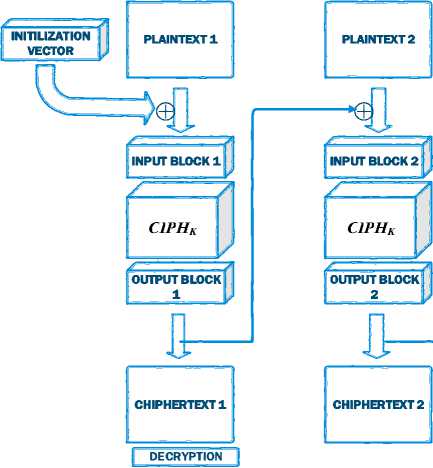
Second mode is the CBC (Cipher Block Chaining). On CBC block plaintext is combining with the previous block ciphertext. For the first block plaintext, is combining with Initialization Vector (IV) shown on Figure 5. The formula used is as follows [6]:
Encryption : C1 = CIPHK(P1 ⊕ IV);
Cj = CIPHK(Pj ⊕ Cj-1)
for j = 2 … n.
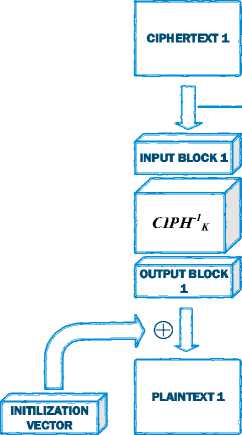
Decryption : P1 = CIPH-1K(C1) ⊕ IV);
P1 = CIPH-1K(Cj) ⊕ Cj-1);
for j = 2 … n.
ENCRYPTION□)

CHIPERTEXT 2

PLAINTEXT 2
CHIPHERTEXT n

PLAINTEXT n
Figure 5. AES CBC
On CFB (Cipher Feedback Mode), IV is used to get an output block. Then the plaintext block is XOR with the output block but only using s most significant bit from the output block where s is an integer parameter. The remaining bit will be discarded shown on Figure 6. The formula used is as follows [6]:
|
Encryption : |
I1 = IV; Ij = LSBb-s(Ij-1) | C#j-1 for j = 2 … n. Oj = CIPHK(Ij) for j = 1, 2 … n. C#j = P#j ⊕ MSBs(Oj) for j = 1, 2 … n. |
|
Decryption : |
I1 = IV; Ij = LSBb-s(Ij-1) | C#j-1 for j = 2 … n. Oj = CIPHK(Ij) for j = 1, 2 … n. P#j = C#j ⊕ MSBs(Oj) for j = 1, 2 … n. |
ENCRYPTION ∏∣
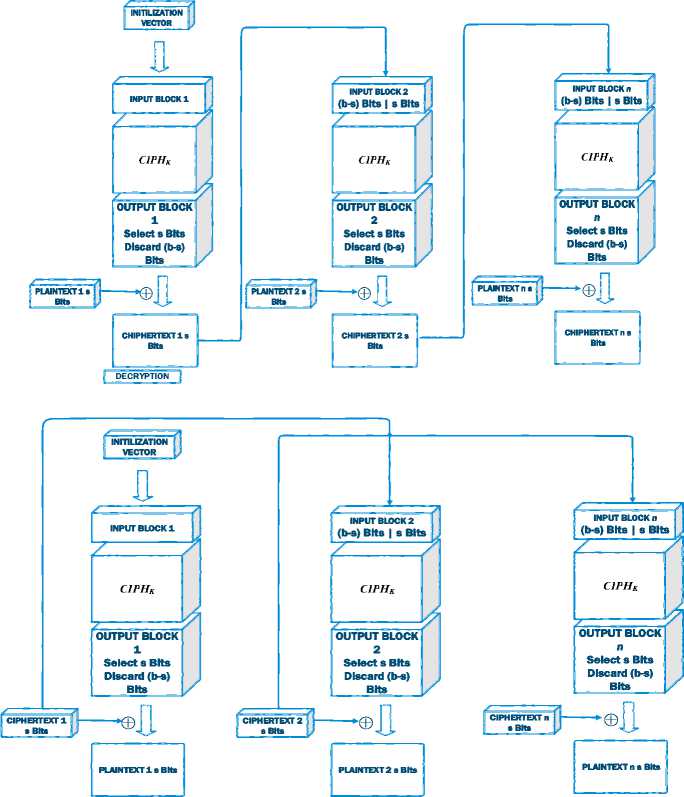
Figure 6. AES CFB
This web hosting will be used to receiving the encryption password from the victim using the php script in Figure 7.
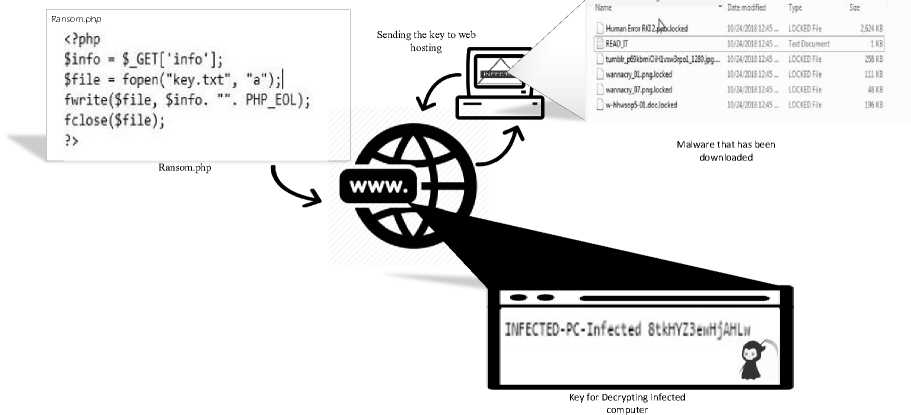
Figure 7. Online Mode
When the program is executed, file will be open by itself and opening its own contain. After file is opened, files on computer are encrypted in the time that has determine before. Then there will be txt file on the desktop that contain information that all your files are encrypted and your payment using address from cryptocurrency. The encryption key is saved in the Flash Drive in txt in Figure 8.
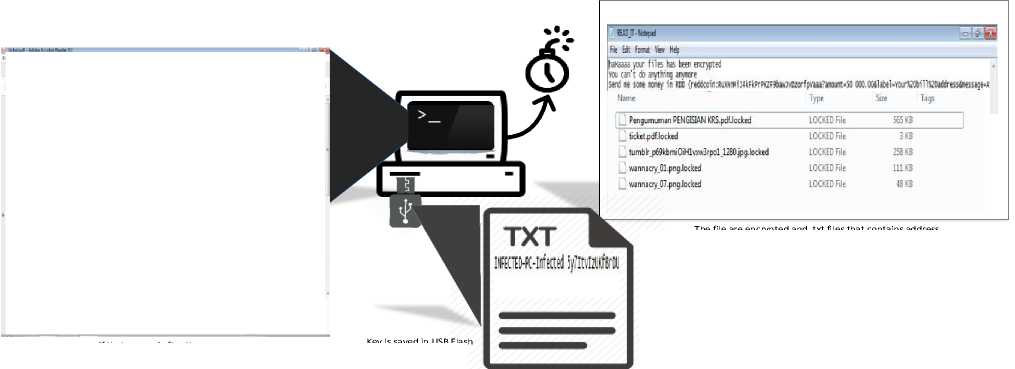
The file are encrypted and .txt files that contains address payment are made after the time has passed
Key is saved in USB Flash Drive
Figure 8. Offline Mode
.pdf that opened after the program is executed
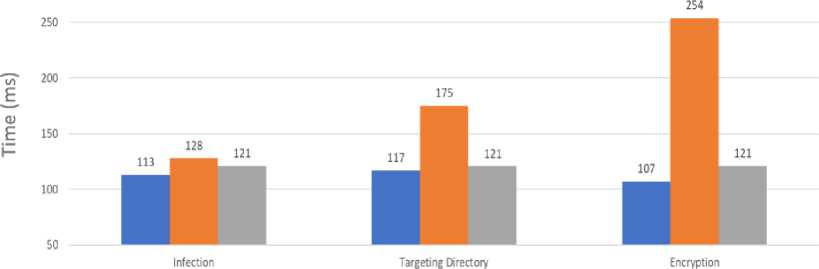
In Table 1. shows the result of test using AES in ECB, CBC and CFB mode for encryption. Time measurement is on millisecond.
Time Comparison
300
■ ECB ∣CBC acre
Table 1. Time Comparison
On ECB each block is encrypted using the same key. Meanwhile on CBC block plaintext is combining with the previous block ciphertext. The first block on CBC in combining with IV. On the other hand, CFB is using IV to get an output block. Then the plaintext block is XOR with the output block but only using s most significant bit from the output block where s is an integer parameter. The remaining bit will be discarded. On infection, ECB is 15ms more faster than CBC and 8ms faster than CFB. On targeting directory, ECB is 58ms more faster than CBC and 4ms faster than CFB. For encryption ECB is way faster with 47ms differences with CBC and 14ms differences with CFB. Therefore, the ECB is faster than CBC and CBC are faster than CFB.
ECB mode is faster than both CBC and CFB because ECB is resulting the same block chipper from the encrypted block. Because of that, if there is a repetitive text it will be ease to recognize. Meanwhile in CBC and CFB both are using Initialization Vector (IV) for XOR operator. With this the encryption result is always unrecognize or jumble even if that massage a repetitive one.
References
-
[1] ORGANISATION FOR ECONOMIC CO-OPERATION AND DEVELOPMENT “Malicious Software (Malware): A Security Threat to the Internet Economy” Ministerial Background Report DSTI/ICCP/REG(2007)5/FINAL.
-
[2] TrendLabs The Global Technical Support & R&D Center of TREND MICRO; “Ransomware: Past, Present, and Future” TREND MICRO 2017.
-
[3] Savage Kevin, Coogan Peter, Lau Hon; “The evolution of ransomware” Symantec version 1.0 August 6, 2015.
-
[4] Federal Information Processing Standard (FIPS). “ADVANCED ENCRPTION STANDARD (AES). Publication 197 November 26, 2001.
-
[5] Gupta Monika, Mahto Swapnil, Patel Ambresh. “Implementation of 128, 192 & 256 bits Advanced Encryption Standard on Reconfigurable Logic”. International Journal of
Engineering Trends and Technology (IJETTI) vol 50 num 6 August 2017
-
[6] Dworkin Morris. “Recommendation for Block Cipher Modes of Operation”. National Institute of Standards and technology (NIST) Special Publication 800-38A 2001 Edition.
23
Discussion and feedback