Information System For Web Based-Report Household Violence In Denpasar
on
Journal of Electrical, Electronics and Informatics, Vol. 2 No. 1, February 2018
15
Information System For Web Based-Report Household Violence In Denpasar
1Yoga Divayana, 2Linawati, 3N.M.A.E.D. Wirastuti, 4Luh Ika Dhivtyasari Suryani
-
1,4Electrical Engineering Department
Faculty of Engineering, Udayana University
Bali, Indonesia
1yogadivayana@gmail.com 4ikadhivtyasari@gmail.com 2,3Telecommunication System Laboratory Electrical Engineering Department Faculty of Engineering, Udayana University Bali, Indonesia 2linawati@unud.ac.id
Abstract Domestic violence is the most common case in the community. Women and children are victims of domestic violence. In Denpasar, Indonesia, currently, data collection system of victims of domestic violence (KDRT) is conducted by the Women's Empowerment and Child Protection Agency. It is still has some limitations because it is operating manually. Through this web-based data collection system of domestic violence, a complaint report on domestic violence can be done digitally so it does not need to report manually to the authorities. In this system, the victims will be given freedom to show or hide their identity. This system receives input filled form of violent reports; next, the complaints report can be known by others (not admin) anonymously. After the complaint report get into in the system, it will be done the next process which is verification. The results of the verification process will determine the validity of complaint reports. After passing the verification process, report data will be recorded in the system and will be done the formulation of follow-up to the action of the case by the legislation authorities.
Index Terms—Violence, Household, Information System, Web.
-
I. INTRODUCTION
Currently domestic violence is a fairly common case in the community. Women and children dominate the number of victims of domestic violence. At present the system of data collection of victims of domestic violence (KDRT) conducted by the Women's Empowerment and Child Protection Agency of Denpasar City still using manual system.
Victim data was collected at the village level, where the victim reporting data was recorded manually, then data from each village head were recorded by the Women's Empowerment and Child Protection Agency. Such a data collection system takes a long time and is less effective. Therefore, it is necessary to develop a system of information system of victims of web-based KDRT data to improve the speed and quality of service. Data collection through web-based information system is also expected to increase public awareness to report cases of domestic violence in their environment either as victim or person nearest victim, because reporting system easier and security of victim identity is guaranteed. In addition to the problems in the process of data collection of victims of domestic violence that has been done to date is still manual, the reluctance of victims of violence or others who witnessed the
violence to report this action to the authorities. So this is also a constraint in the process of data collection of acts of violence in the household.
Through this web-based data collection system of domestic violence, a complaint report on domestic violence can be done directly without having to go to the authorities to help deal with the problem. In this system will also be given freedom to the victim who reported the complaint (user) to display their identity or want to hide it. To know the reported data is valid or not the admin can know through the data selfinserted first by the user at the time of Sign Up.
-
II. LITERATURE REVIEW
-
2.1 Case of Violence in the Household (KDRT)
Referring to Law no. Law No. 23 of 2004 concerning the Elimination of Domestic Violence, an act of domestic violence is an act against a person, especially a woman, resulting in physical, sexual, psychological and / or neglect of misery or suffering of households including acts, coercion or robbery independence against the law within the scope of the household. This disadvantage is increasingly growing, so that with the existence of Law No.23 of 2004 the act of violence in the household can be reduced.
However, until now the recording or data collection on domestic violence cases has not been fully transparent. Where it happens because of the reluctance of the victim to report on acts of violence in the household to the authorities. Thus the Women's Empowerment and Child Protection Agency has an important role in data collection and communications closely with victims of domestic violence. The mission of the Women's Empowerment and Child Protection Agency of Bali Province specifically concerning domestic violence is to provide protection and eliminate all forms of violence in the household against women and children.
-
2.2 Information System
The system is a networking of interrelated procedures, gathered together to perform an activity or to complete a particular target (Jogiyanto, 2005). There are two groups of approaches in defining the system (Jogiyanto, 2005) namely:
-
1. The system approach emphasizes on the procedure, stated by Jerry Fitz Gerald, Ardra F.Fitz Gerald, Warren D.Sallallings Jr., that: "A system is a network of interrelated procedures, gathered together to perform an activity or to complete a specific goal ".
-
2. The system approach which is the network of procedures more emphasizes on the order of operations within the system, that a system is a collection of elements that interact to achieve a purpose.
Information is data that has been classified or processed or interpreted for use in the decisionmaking process (Sutabri, 2005). An Information System is a collection of computer hardware and software as well as human devices that will process data using such hardware and software. In addition data also plays an important role in the information system. The data to be entered is an information system that can be form forms, procedures and other forms of data. (Andri Kristanto, 2003). The information system can be defined as follows:
-
1. A human-made system consisting of component components within an organization to achieve a goal of presenting information.
-
2. A set of organizational procedures that at the time of execution will provide information to decision makers and to control the organization.
-
3. A system within an organization that meets the needs of transaction processing, supporting operations, managerial and strategic activities of an organization and providing certain external parties with the necessary reports. (Andri Kristanto, 2003)
-
2.3 Database
The database is a collection of related or related data. According to Scott (2004: 349) database is a computer file system that uses the way of organizing files, intended to facilitate and accelerate access to all data through the application program. The objectives
of a database presented by Murdick, Ross and Claggett (1997: 158) include:
-
1. Provide mass storage for relevant data.
-
2. Facilitate users in obtaining or accessing data.
-
3. Allows an immediate response to data requests from users.
-
4. Make last modification immediately to the data.
-
5. Ease in removing excessive data.
-
6. Allows simultaneous use by multiple users.
-
7. Allows for further development in the database system.
-
8. Protect data from physical damage and unauthorized use.
The main principle of the database is the arrangement of data, while the main purpose of the database is the ease and speed in data retrieval. It is important for a SIM to have organized and structured data sources in a logical way, so that data can be easily accessed, processed efficiently, retrieved quickly, and managed effectively.
-
2.4 Basic Concept of Data Collection
According Susanto (2002: 73) "Data is a
description of a thing, can be a known or considered or perceived". Or data is a fact or anything that can be used as input in generating information described through numbers, symbols, codes, and others.
Data collection is the process of data processing or manipulation of data or transformation of symbols such as numbers and alphabets for the purpose of increasing its usefulness or produce information about more precise and useful. Data is also a process in obtaining concise data or certain formulas.
According to Hasan (2004: 37) as for the data processing includes the following activities:
-
1. Editing, is a check or correction of data that have been collected because of the possibility of incoming data is not logical or doubtful.
-
2. Coding, is the giving or making of codes on each data in the same category.
-
3. Tabulation, is to create tables containing the data that has been given the code in accordance with the required analysis.
-
2.5 Web Server
Web server is an application program that has a function as a place to store web documents. All web documents are stored in the main web server directory ie document root (Rudyanto, 2011: 19). A web server is not always suitable for a particular platform or operating system. Most web servers, especially paid type web servers, are only suitable for certain operating systems only. One of the web servers capable of supporting multiple operating systems is Apache, where Apache is capable of running on multiple operating systems such as Microsoft Windows, Linux, Solaris, Mac OS X. Apache is an open source software developed by an open
community of developers in under the auspices of the Apache Software Foundation.
-
2.6 Database Server
Database server is an application program used to store data to be processed in web pages (Rudyanto, 2011: 20). The use of database server is able to support the security, data recovery, use of interfaces, and processing of data in the database easily and quickly. One of the most famous and widely used database server for building web applications is MySQL. MySQL (MY Structured Query Language) is a database creation and management program or so-called DBMS (Database Management System), the nature of DBMS is Open Source (Nugroho, 2008). MySQL is the first database server supported by the programming language for the internet, developed by MySQL AB around 1994-1995. In addition to being open source and free on various platforms, MySQL popularity is due to the ease of accessing the database, fast query performance, and sufficient for the needs of medium-scale enterprise databases.
-
III. METHODS
-
3. 1 Research Method
The domestic violence data collection system will use the web base. Flow chart research can be seen in Figure 3.1.
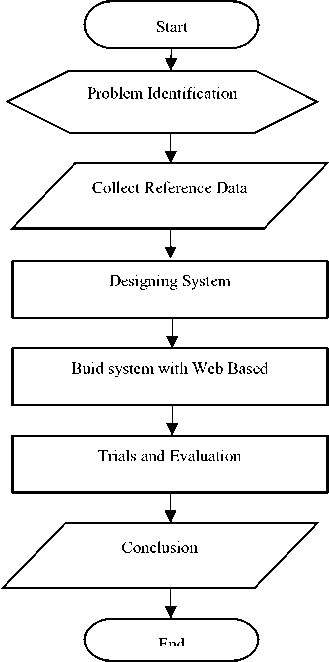
Fig 1. Research Flow Chart
The explanation of the flow chart in Figure 4.1 is as follows:
-
1. Identify the problem, identify problems that exist when there are obstacles in the process of data collection of an action manually.
-
2. Collection of reference data, collecting references needed to support the research to be conducted.
-
3. System modeling, modeling phase of the system will design the input-output elements and processes of the system.
-
4. Making information systems, processes undertaken to build and mebuat a data collection system that will be tested and evaluated its success.
-
5. Testing and evaluation process, in this process will be tested by conducting the next complaint report will be verified by the admin about the validity. Subsequent summary results will be evaluated to determine the success rate of information systems in verifying and recording the existence of acts of violence in the household.
-
6. Taking conclusions, stages of conclusion from some data input system that has been processed on the system to draw conclusions from research conducted.
-
3. 2 System Design
The data collection system of domestic violence will be designed web-based. Overview of the system to be made can be seen in Figure 4.2. In general, this system has steps that is, accept input in the form of reports of complaints of violent acts by filling in the data themselves first, next report complaints inputted can be done and can be known by others (not admin) anonymously, after the complaint report went into in the system will be done the next process of verification. The results of the verification process will determine the validity of complaint reports that enter into the system. After verification and report data is valid it will be recorded in the system and will be done the formulation of follow-up to the action of the case by the authorities in accordance with the legislation.
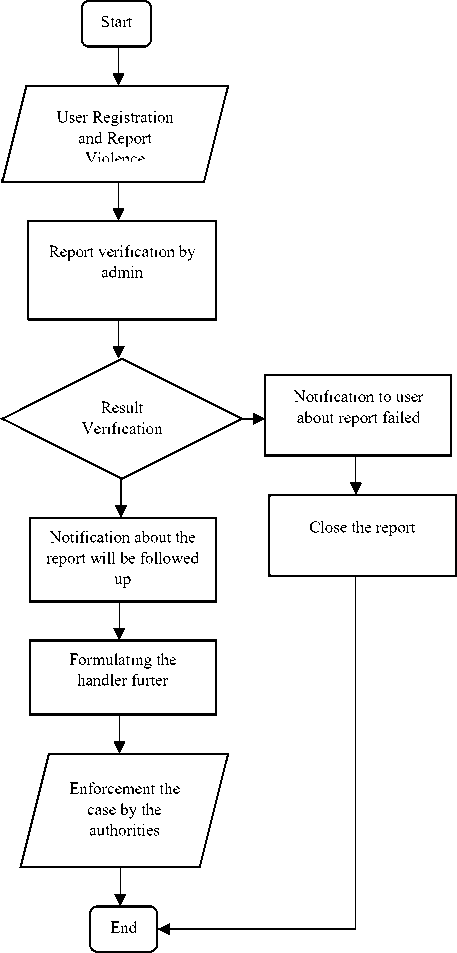
Fig 2. Violence Report System Flow chart
database is divided into several entities as in the following figure
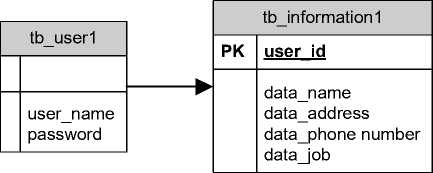
Fig 3. Database Design
In the information system data collection of violence in this household, used data flow diagram as follows
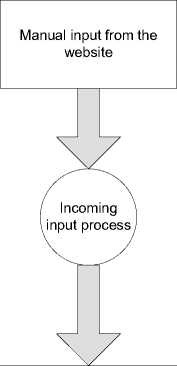
Reporting data from the website
Fig 4. Block Diagram of Violence Report System
The following is a general explanation from the reporting system of violence in household
The system testing planning will be done with the following scenario:
-
1. If user can login normally or can enter into system and do reporting.
-
2. If the user has failed Login or entered into the system so can not perform reporting.
-
3. If the internet network is disconnected when about to submit submit reporting.
-
IV. DESIGN AND RESULTS
In the information system of data collection of violence in this household, used several databases that describe data managed by the system, ranging from user identity data, to data reporting. The use of this

Fig 5. General Explanation of Violence Report System
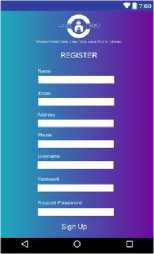
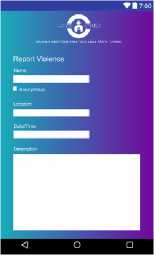
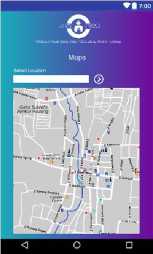
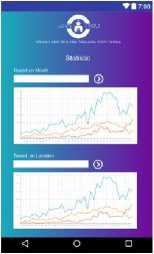
Here is the layout design of the website that will be created to support the violent reporting system

(a)
(b)

(c)

(d)
(e)
(f)
(g)
Fig 6. Interface Design of Violence Report Android Application
The conclusions obtained from the above exposure of the design of reporting system of violence is implemented in the form of Website and data reporting results will be stored in the database. This reporting system of violence is carried out by means of reporting mechanisms committed by victims and other reporters, will enter into the database recording of violence and identity of the reporter and the victim will be disguised so as to protect the privacy rights of victims and reporters, as well as providing security of rights victim privacy and complainant.
As for suggestions that can be given by the authors in this research that should be done to the aspect of implementation of the system such as one example makes this system can be implemented in mobile either using Android platform, IoS, GSM, or others. As well as strengthening the identity security methods of reporters and victims reported by using other methods.
REFERENCES
-
[1] Adelia et al. 2011. Implementation of Customer
Relationship Management (CRM) on Hotel Reservation System based on Website and Desktop.
-
[2] Andri Kristanto. 2003. Design of SI and its Application.
Yogyakarta: Publisher Gava Media
-
[3] Arief, M. Rudyanto. (2011). Dynamic Web Programming
Using PHP and MySQL. Yogyakarta: Andi.
-
[4] Budi Raharjo, et al. 2010. Web Programming Module
(PHP, HTML, MYSQL). Bandung: Modula.
-
[5] Hasan. 2004. Analysis and Research with Statistics.
Publisher PT. Jakarta: Earth Literacy.
-
[6] Ikhwan Chandra, et al, (2007) Administration System of
Puskesmas Puskesmas Merapi II using TAS Method.
-
[7] Jogiyanto, H.M. 2005. Analysis and Design of Information
Systems Structured Approach Issue III. Yogyakarta: Andi Offset.
-
[8] Nugroho, Bunafit. (2008). Exercise Create PHP and
MySQL Web Applications with Dreamweaver MX (6, 7,2004) and 8. Yogyakarta: Gava Media.
-
[9] Susanto. 2002. Management Information System Concepts
and Development. Padjadjaran University. Bandung: Publisher Unggu Jaya.
-
[10] Sutabri, Tata. 2005. Management Information System.
Yogyakarta: Andi Offset.
-
[11] Sutarman. 2003. Building Web Applications with PHP and
MySQL. Publisher Graha Ilmu: Yogyakarta.
Discussion and feedback